Why Your Business Needs a Cyber Security Threats Assessment Now More Than Ever
A cyber security threats assessment is a systematic process to identify, evaluate, and prioritize potential digital threats that could harm your organization’s data, systems, and operations. Here’s what you need to know:
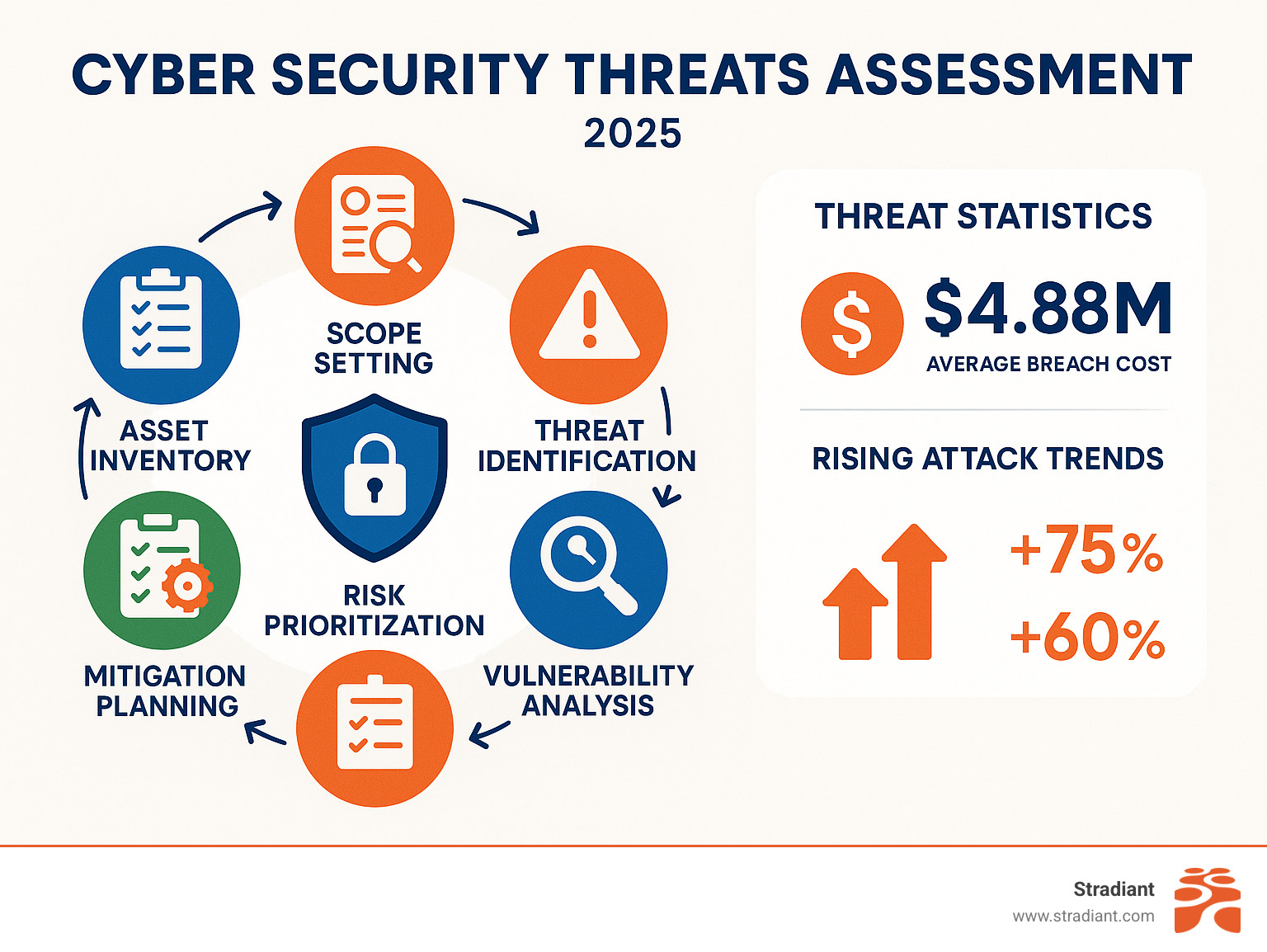
Key Components of a Cyber Security Threats Assessment:
- Asset identification – Cataloging critical systems, data, and infrastructure
- Threat analysis – Identifying potential attack vectors and threat actors
- Vulnerability evaluation – Finding security gaps in your defenses
- Risk prioritization – Ranking threats by likelihood and business impact
- Mitigation planning – Developing strategies to reduce identified risks
The numbers tell a stark story about today’s threat landscape. Organizations face an average cost of $4.88 million per data breach in 2024, while cloud intrusions have surged 75% and interactive attacks like credential phishing have jumped 60% in just one year.
These aren’t just statistics – they represent real businesses that suffered devastating losses because they didn’t understand their threat exposure. Without a proper assessment, you’re essentially flying blind in a digital minefield.
The good news? A structured approach to threat assessment can transform your security posture from reactive to proactive, helping you stay ahead of attackers instead of scrambling after an incident.
I’m Joe Dunne, and I’ve spent years helping organizations steer complex cybersecurity challenges through my experience as an IT Director and now as founder of Stradiant. Regular cyber security threats assessment has become essential for every business I work with, regardless of size or industry.
What is a Cyber Security Threats Assessment?
Think of a cyber security threats assessment as your organization’s digital health checkup. It’s a formal evaluation process that systematically identifies and analyzes potential threats to your information systems and data. According to NIST SP 800-30, it’s defined as “the process of formally evaluating the degree of threat to an information system or enterprise and describing the nature of the threat.”
A proper cyber security threats assessment goes beyond simple vulnerability scanning. It’s a comprehensive examination that considers the full spectrum of threats your business faces, from sophisticated ransomware groups to employees who might accidentally click on phishing emails.
The assessment examines both internal and external threats, evaluates how likely they are to occur, and assesses their potential impact on your business operations. This includes everything from malware and ransomware to insider threats and social engineering attacks.
Key objectives include understanding your unique threat landscape, cataloging potential attack vectors, evaluating threat capabilities, prioritizing security investments, and meeting compliance requirements for regulatory frameworks like HIPAA, PCI-DSS, or GDPR.
Cyber Security Threats Assessment vs. Risk Assessment
People often use these terms interchangeably, but they serve different purposes. A cyber security threats assessment focuses on identifying and analyzing potential threats, while a risk assessment evaluates the probability and impact of those threats on your business.
| Aspect | Threats Assessment | Risk Assessment |
|---|---|---|
| Primary Focus | Identifying potential threats and attack vectors | Evaluating probability and business impact |
| Scope | Threat actors, attack methods, vulnerabilities | Asset value, likelihood, consequences |
| Output | Threat catalog and analysis | Risk register with prioritized actions |
Think of it this way: a threats assessment answers “what could attack us and how?” while a risk assessment answers “what’s the likelihood and cost if they succeed?”
Why Organizations Need Regular Cyber Security Threats Assessment
The threat landscape changes rapidly, making regular assessments critical. We recommend conducting assessments at least annually, or whenever you make significant changes to your environment.
Financial protection should be your first consideration. With the average data breach costing $4.88 million in 2024, the investment in assessment looks smart compared to potential losses.
Regulatory compliance isn’t optional. Many frameworks require formal threat assessments, including GDPR, HIPAA, and PCI-DSS. Non-compliance can result in fines reaching millions of dollars.
Business continuity depends on understanding what could disrupt operations, while reputation management protects against the trust damage that takes years to rebuild after a breach.
Mapping Today’s Top Cybersecurity Threats in 2025

The cybersecurity landscape in 2024 feels like a digital Wild West, where threats evolve faster than most organizations can adapt. After working with countless businesses across Central Texas, I’ve seen how these threats impact real companies.
Ransomware has become the nightmare that keeps business owners awake. Modern ransomware groups use double extortion tactics, stealing data before encrypting it, then threatening to publish sensitive information. The average recovery cost has hit $2 million, not counting the ransom itself.
Credential-based attacks represent low-hanging fruit that cybercriminals love. Password spraying, credential stuffing, and sophisticated phishing campaigns are exploding because they work. When someone clicks that convincing fake login page, attackers suddenly have legitimate access.
The 75% increase in cloud intrusions reflects how quickly attackers adapted to our cloud shift. Misconfigured cloud settings, unsecured APIs, and weak identity management create perfect entry points.
AI-powered attacks use artificial intelligence to craft convincing phishing emails and create deepfake audio for social engineering calls. These tools make novice attackers look like experts.
Social engineering remains devastatingly effective because it targets the human element. Insider threats create challenging dynamics, whether from disgruntled employees or accidental clicks.
Most Prevalent Threat Vectors & Recent Statistics
The 60% increase in interactive intrusions shows attackers are getting more hands-on. These aren’t automated attacks – they’re calculated, human-driven operations that adapt to your defenses in real-time.
Credential phishing has become an art form, with attackers creating identical login pages complete with proper branding and SSL certificates. Password spraying attacks target common passwords like “Password123!” against hundreds of accounts.
Supply chain attacks hit organizations through trusted vendors, while IoT vulnerabilities multiply as organizations add connected devices without proper security planning.
Using Threat Intelligence to Stay Ahead
Effective threat intelligence transforms your cyber security threats assessment from guesswork into strategic defense. The MITRE ATT&CK framework provides common language for understanding attacker operations, while the National Vulnerability Database offers comprehensive vulnerability information with severity scores.
CISA’s Risk and Vulnerability Assessments provide insights into real-world attack patterns, and commercial threat intelligence feeds deliver real-time information about emerging threats. The key is connecting these intelligence sources to your specific environment and risk profile.
Step-by-Step Guide: Performing a Cyber Security Threats Assessment

Conducting a thorough cyber security threats assessment doesn’t have to feel overwhelming. The most successful assessments follow a clear, methodical approach, taking it one step at a time with the right people involved.
Step 1 – Set Scope and Assemble a Cross-Functional Team
Define your boundaries clearly. Are you examining just your main office or including remote workers? Which systems are in scope – core business applications, cloud services, or everything including legacy systems?
Get the right team together. You’ll need IT folks who understand system connections, security team members who know vulnerabilities, and business representatives who understand operational priorities. Include someone from legal or compliance for regulatory requirements.
Executive sponsorship isn’t optional. Without leadership buy-in, you’ll struggle to get necessary resources and cooperation.
Step 2 – Build & Classify an Asset Inventory
Start with your “crown jewels” – assets that would hurt most if compromised. This includes customer databases, financial systems, intellectual property, and core applications that keep your business running.
Classify everything by business impact. Some assets are mission-critical, others important but not devastating, and some nice-to-have. This classification helps focus protection efforts where they matter most.
Map dependencies. That seemingly minor system might be critical if it supports essential business functions.
Step 3 – Identify Potential Threats and Vulnerabilities
Use vulnerability scanners to identify technical weaknesses like unpatched software, misconfigured settings, and weak passwords. These tools find obvious problems but are just the starting point.
Consider the human element. Social engineering attacks exploit our natural helpfulness. Assess team susceptibility to phishing emails, phone scams, or unauthorized physical access. This is where Cybersecurity Awareness Training becomes invaluable.
Research external threats specific to your industry and region. Different sectors face different risks.
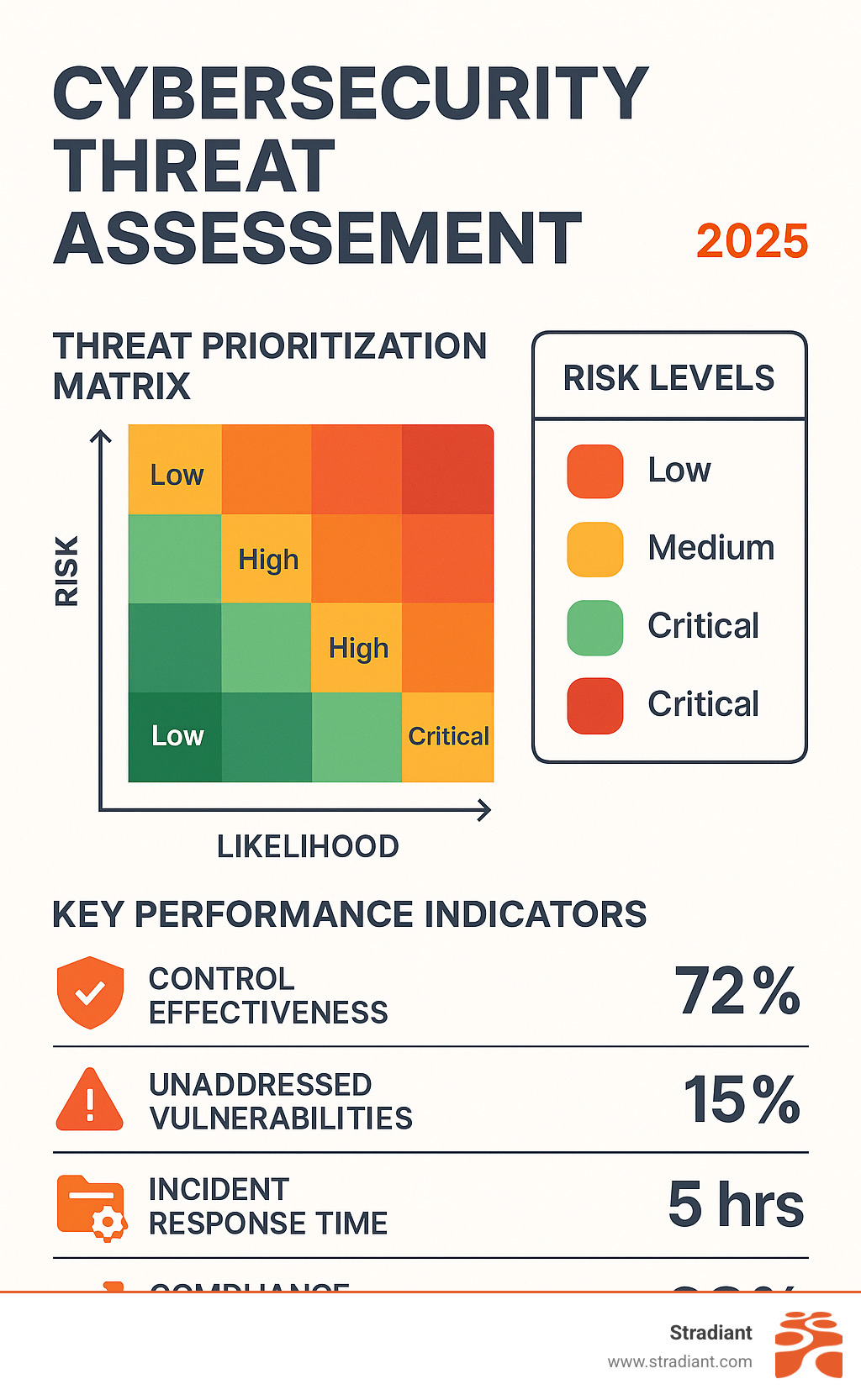
Step 4 – Analyze Likelihood and Impact
Create a risk matrix plotting likelihood against impact. High likelihood, high impact threats need immediate attention. Translate risks into financial terms whenever possible – revenue loss from downtime, breach notification costs, legal fees.
Consider cascading effects. Ransomware doesn’t just encrypt files – it disrupts operations, damages reputation, and affects customer trust.
Step 5 – Prioritize and Implement Controls
Multi-factor authentication tops the quick wins list, stopping most credential-based attacks. Regular patching eliminates many attack vectors, while employee security training addresses human factors.
Network segmentation limits attack spread, and backup procedures ensure recovery capability.
Step 6 – Document, Report & Monitor
Create a risk register documenting every identified threat with impact, current controls, and recommended improvements. Develop an executive summary focusing on business impact and implementation priorities.
Establish ongoing monitoring to track progress, watch for new threats, and measure improvements.
Tools, Frameworks & Methodologies That Make Assessment Easier
Established frameworks transform overwhelming cyber security threats assessment complexity into manageable, systematic processes. Think of these as your roadmap through the assessment wilderness.
NIST Cybersecurity Framework 2.0 has become the gold standard with six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. Its flexibility allows adaptation to your organization’s size and complexity.
MITRE ATT&CK Framework maps real-world attack techniques used by actual threat actors, providing concrete scenarios rather than theoretical possibilities.
ISO 27001 offers formal certification and comprehensive documentation, often satisfying multiple compliance requirements simultaneously for regulated industries.
STRIDE methodology breaks threats into six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
CISA CSET® (Cyber Security Evaluation Tool) provides free, structured guidance throughout the assessment process, particularly valuable for critical infrastructure organizations.
For comprehensive methodology guidance, the NIST SP 800-30 Rev. 1 document provides detailed technical specifications.
Choosing the Right Framework
Start with industry requirements. Certain frameworks may be mandated by regulation in healthcare, financial services, or government contracting.
Consider security maturity. NIST CSF 2.0 provides excellent coverage without requiring advanced security expertise for implementation.
Evaluate available resources honestly. Some frameworks require significant time investment and specialized knowledge.
Many successful organizations combine elements from multiple frameworks rather than rigidly following just one.
Integrating MITRE ATT&CK
MITRE ATT&CK transforms threat assessment from guesswork into intelligence-driven analysis. Map current defenses against the ATT&CK matrix to reveal surprising gaps. Use threat intelligence to prioritize which techniques deserve immediate attention. Test detection capabilities by simulating ATT&CK techniques in your environment.
Maintaining, Updating & Leveraging Assessment Results
Your cyber security threats assessment isn’t a shelf-sitting report – it’s a living document driving real security improvements. Treat it as an ongoing process rather than a one-time event.
We recommend comprehensive assessments annually, with quarterly updates for highest-risk areas. Major system changes, new threats targeting your industry, regulatory changes, and major security incidents affecting similar organizations should trigger immediate updates.
Continuous monitoring transforms your assessment from a snapshot into real-time security visibility through automated vulnerability scanning, threat intelligence feeds, and monitoring systems.
For comprehensive support with ongoing threat assessment management, learn more about how we can help you protect your business from cyber threats.
Turning Findings Into Actionable Security Improvements
Start with a security roadmap prioritizing improvements based on risk level and available resources. Tackle improvements in manageable chunks rather than trying to fix everything at once.
Budget alignment is crucial. Time your assessment to inform budget planning cycles, focusing on business impact rather than technical details when presenting to leadership.
Validate that new controls work through regular testing, including penetration testing, tabletop exercises, or simulated phishing campaigns.
Measure progress with meaningful metrics demonstrating security posture improvements over time.
Common Challenges & How to Overcome Them
Data overload affects organizations facing massive amounts of security alerts and findings. Focus on business impact rather than technical severity, using automated tools to filter and correlate results.
Lack of expertise affects smaller businesses without dedicated security teams. Consider partnering with external specialists, investing in staff training, or leveraging managed security services.
Internal resistance can derail initiatives. Address this by communicating business benefits, involving resistors in the process, and demonstrating quick wins.
Tool sprawl creates confusion when organizations deploy multiple unintegrated security tools. Conduct regular tool audits and standardize on integrated solutions.
Real-World Examples, Templates & Resources
Real-world experiences show how cyber security threats assessment saves businesses from disaster. Organizations taking threat assessment seriously fare much better when attacks come.
A regional bank’s assessment revealed employee vulnerability to credential phishing and inadequate email filtering. They implemented multi-factor authentication, upgraded email security, and ran phishing simulation training. Six months later, when sophisticated phishing swept their industry, employees recognized and reported attacks immediately while other institutions suffered breaches.
A medical practice’s assessment uncovered critical backup vulnerabilities and improper network segmentation – medical devices on the same network as administrative systems. They implemented offline backups, isolated medical devices, and deployed endpoint detection. When ransomware struck a neighboring practice, causing weeks of downtime, the assessed practice continued operating normally.
A local government agency’s assessment identified public websites as prime denial-of-service targets. They implemented DDoS protection and developed incident response procedures, successfully defending against multiple attacks during a contentious election period.
For professional guidance through this process, our comprehensive Cybersecurity Risk Assessments help identify and address vulnerabilities before they become costly incidents.
Downloadable Threat Assessment Templates & Checklists
Scope Definition Worksheet helps clearly define assessment boundaries and stakeholder involvement, including asset inventory templates and timeline planning.
Risk Assessment Matrix provides frameworks for structured decision-making with likelihood and impact scoring criteria, risk level definitions, and treatment decision frameworks.
Threat Catalog Template organizes potential threats covering common categories, industry-specific threats, and threat actor profiling.
Executive Report Outline ensures findings reach decision-makers through executive summaries, risk visualization charts, and recommendation prioritization.
Mitigation Planning Template bridges assessment and action with control selection criteria, implementation timelines, and success metrics.
Frequently Asked Questions about Cyber Security Threats Assessment
How often should we perform a cyber security threats assessment?
At least once a year as your baseline, with quarterly mini-assessments for highest-risk areas. High-risk industries like healthcare, finance, and critical infrastructure need more frequent evaluations. Regulatory requirements often dictate minimum frequencies. Major organizational changes should trigger additional assessments – new systems, relocations, mergers, or significant process changes can introduce new vulnerabilities.
Can parts of the assessment be automated effectively?
Absolutely. Automation excels at heavy lifting tasks like vulnerability scanning, asset findy, threat intelligence feeds, basic risk scoring, and report generation. However, business impact analysis, threat actor motivation assessment, and strategic risk decisions require human judgment. The sweet spot is using automation for data collection and basic analysis, then applying human expertise for context and strategic thinking.
What is the first step if we’ve never done an assessment before?
Begin with a basic asset inventory – make a list of critical systems, important data, and essential applications. Get your team on board early with a kickoff meeting including IT, operations, and business stakeholders. Start with obvious risks like outdated software, weak passwords, or lack of security training. Consider getting help from experienced security professionals for your first assessment. Document everything with simple templates you can improve over time. The perfect assessment is the enemy of the good assessment – start with basic evaluation and improve over time.
Conclusion
A well-executed cyber security threats assessment isn’t just another IT checkbox – it’s your organization’s lifeline in an increasingly dangerous digital world. With data breaches averaging $4.88 million in costs and cybercriminals getting craftier daily, the assessment cost is pocket change compared to devastating attack damage.
The systematic approach we’ve covered – from setting clear scope and building asset inventories to implementing targeted controls and maintaining vigilant monitoring – provides a proven roadmap for understanding and neutralizing cyber threats. Whether dealing with ransomware, credential thieves, cloud exploits, or human error, thorough assessment provides the visibility and strategic direction you need.
Cyber security threats assessment isn’t “set it and forget it” – it’s like tending a garden, requiring continuous nurturing and adaptation as conditions change. The threat landscape evolves faster than fashion trends, and your defenses must keep pace.
Regular assessments, combined with continuous monitoring and fresh threat intelligence, create a proactive security posture. Instead of scrambling after attackers break down your digital door, you’re anticipating their moves and blocking them before they cause damage.
The investment pays dividends beyond avoiding breaches: improved compliance scores, better business continuity, and increased stakeholder confidence. Your customers trust you more, employees feel safer, and leadership gains strategic insights for smart security decisions.
Start with the fundamentals outlined here, leverage proven frameworks and tools, and build a sustainable program that grows with your business. Don’t try to boil the ocean on day one – begin with critical assets and expand as confidence and capabilities grow.
Don’t wait for a security incident to reveal vulnerabilities. Take control of your threat landscape today through systematic assessment and proactive defense.
For organizations ready to take cybersecurity seriously, Stradiant’s 24/7 experts can streamline your threat assessment process and provide ongoing protection custom to your specific needs. We understand that small and medium-sized businesses need enterprise-level security without enterprise-level complexity or cost.
Ready to transform your security posture from reactive to proactive? Learn more about our comprehensive Cybersecurity Risk Assessments and find how we can help protect your business with solutions designed specifically for organizations like yours.

