Understanding the Phishing Threat
Learning how to prevent phishing attacks is vital. Phishing is a cyber-attack where scammers try to trick you into giving them your personal information or money. They use fake messages that look like they come from trusted sources, like your bank or a company you know.
These attacks are very common. Cybercriminals use them because they are cheap to launch and often succeed. Thousands of phishing attacks happen every day, making them one of the most widespread types of cybercrime. They lead to stolen passwords, identity theft, financial losses, and can even put harmful software (malware) on your devices.
The good news is you can protect yourself. Here are quick tips on how to prevent phishing attacks:
- Be Skeptical: Always question unexpected messages, especially those asking for urgent action or personal details.
- Check Before You Click: Hover your mouse over links to see the real destination. Don’t click suspicious links or attachments.
- Use Strong Security: Set up unique, complex passwords and turn on multi-factor authentication (MFA) for all your accounts.
- Keep Software Updated: Make sure your operating system, web browsers, and security software are always up to date.
- Report Suspicious Activity: If something feels off, report the message to your email provider or IT department, then delete it.
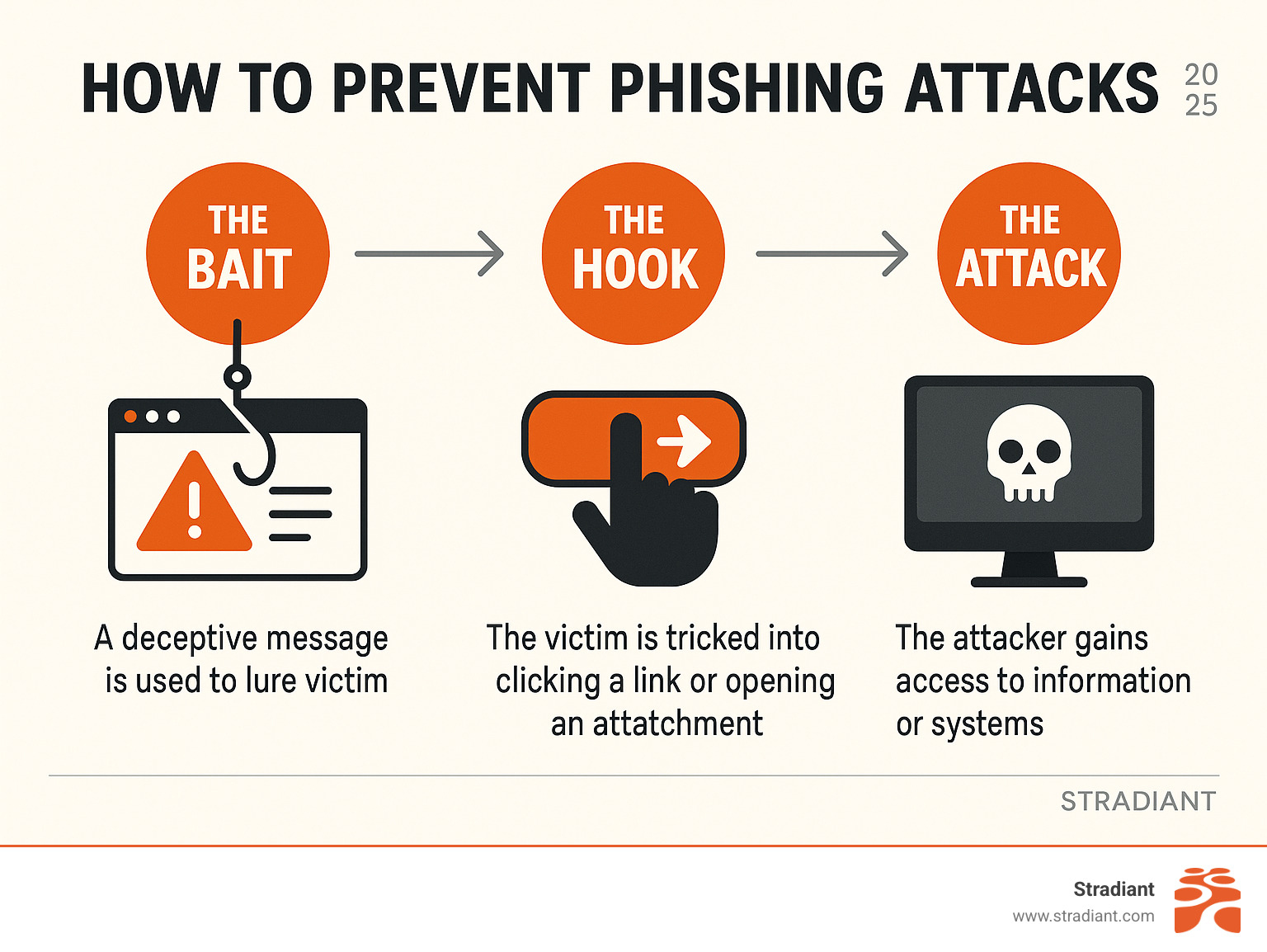
What is Phishing and How Does It Work?
Phishing is a form of online fraud that relies on social engineering to trick you into giving up confidential data or downloading malware. Attackers disguise themselves as trusted entities, create a sense of urgency, and lure victims with “the bait” (a realistic-looking message), “the hook” (a link or file), and finally “the attack” (credential theft, data exfiltration, or ransomware).
For a deeper dive into social-engineering tactics, see Cybercriminals Are Using Social Engineering: Here’s What You Need to Know.
The Different Types of Phishing Attacks
Attackers keep inventing new angles, but most scams fall into one of these categories:
- Email Phishing – Mass emails that push you to click or download quickly.
- Spear Phishing – Highly targeted messages custom with details from social media.
- Whaling – Spear phishing aimed at executives or other “big-fish” decision makers.
- Vishing – Phone calls that impersonate banks, tech support, or government offices.
- Smishing – Similar to vishing but delivered by SMS text.
- Angler Phishing – Fake customer-service accounts on social media.
- QR Code Phishing (Quishing) – Malicious QR codes that send you to rogue sites or drop malware.
- Pharming – Tampering with DNS so a legitimate URL redirects to a fake site.
- Pop-up Phishing – Fake pop-ups on real sites asking for logins or payments.
- Evil Twin – A look-alike Wi-Fi hotspot that captures all traffic passing through it.
How to Recognize the Signs of a Phishing Attempt
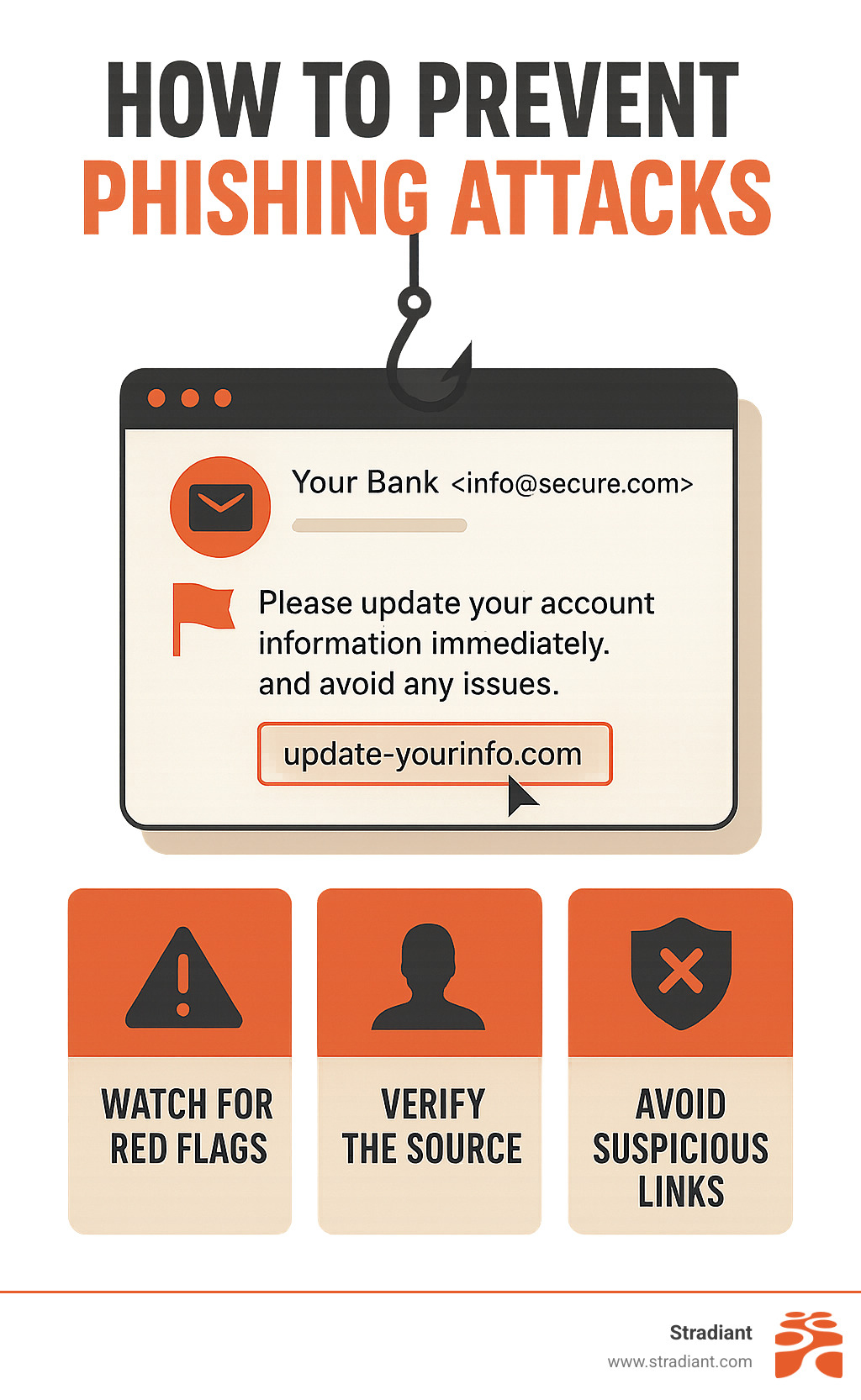
Look for these common red flags:
- Urgent or threatening language (“verify now or lose access”).
- Generic greetings instead of your name.
- Typos or awkward grammar.
- Sender address that almost, but not quite, matches the real domain.
- Links that go somewhere unexpected or use URL shorteners.
- Unsolicited attachments, especially ZIP or EXE files.
- Requests for sensitive data or payments via gift cards/crypto.
- Offers that seem too good to be true.
- Design, logo, or formatting that looks slightly “off.”
If any one of these appears, pause and verify before clicking.
A Multi-Layered Guide on How to Prevent Phishing Attacks
No single tool or policy can block every scam, so Stradiant recommends a defense-in-depth approach: combine smart technology, sound processes, and well-trained people.

How to Prevent Phishing Attacks as an Individual
- Use strong, unique passwords (15+ characters) and store them in a password manager. See How Secure Are Your Business Passwords.
- Enable Multi-Factor Authentication (MFA) everywhere. Even stolen passwords are useless without the second factor.
- Update software promptly. Patches close known holes that malware exploits.
- Back up important data so ransomware can’t hold you hostage.
- Hover before you click and type URLs manually when in doubt.
- Install reputable anti-phishing browser add-ons and keep firewalls on.
- Monitor bank and credit statements for suspicious charges.
- Avoid jailbroken/rooted devices that disable built-in protections.
How to Prevent Phishing Attacks in Your Organization
| Control Type | Technical Controls | Human Controls |
|---|---|---|
| Methods | Email gateways, DMARC/SPF/DKIM, EDR, secure web gateways | Security awareness, clear policies, easy reporting |
| Purpose | Block threats before users see them | Turn staff into an early-warning system |
| Example | Gateway stops 1,750 of 1,800 phishing emails | Employee spots and reports the remaining 50 |
Key actions:
- Deploy advanced email filtering and DMARC/SPF/DKIM to stop spoofed mail.
- Protect endpoints with modern EDR/antivirus.
- Use firewalls and secure web gateways to inspect traffic.
- Maintain a written incident-response plan that spells out who does what if someone clicks.
- For SMBs without a large IT staff, a managed partner like Stradiant can handle 24/7 monitoring and IT Management
The Role of User Education and Its Limitations
Training turns employees into sensors, but it isn’t foolproof. Run regular phishing simulations, reward quick reporting, and avoid blame. A study showed that when 50 phishing emails reached inboxes, 36 were ignored or reported—proof that awareness matters, but technology must still back people up.
What to Do When You Encounter a Phishing Scam
If You Suspect a Phishing Email or Text
- Do not click, open, or reply.
- Verify independently via a known phone number or website.
- Report it:
- Forward phishing emails to
reportphishing@apwg.org. - Forward phishing texts to 7726 (SPAM).
- Tell your employer’s IT or security team.
- Forward phishing emails to
- Delete the message once reported.
If You Already Clicked or Gave Information
- Disconnect from the internet to limit spread.
- Change passwords and enable MFA immediately.
- Notify your bank or credit-card issuer of any exposed financial info.
- Place a fraud alert or credit freeze with Equifax, Experian, and TransUnion.
- Run a full malware scan on all devices.
- Document what happened for insurers, law enforcement, or the FTC.
Stradiant’s Data Backups and Data Recovery services can help restore clean copies fast. Full recovery steps are at What to do if your information is lost or stolen.
Where Else to Report Phishing
- FTC – ReportFraud.ftc.gov or 1-877-IDTHEFT.
- Anti-Phishing Working Group –
reportphishing@apwg.org. - Your email provider – use “Report phishing/spam.”
- Local police – if money or identity was stolen.
The Evolving Threat: Future Trends in Phishing
Phishing is moving from clumsy mass emails to highly polished, personalized deception.
- AI-powered writing generates error-free, custom messages at scale.
- Deepfakes will enable convincing voice or video requests (“urgent wire transfer …”).
- Business Email Compromise (BEC) continues to drive billion-dollar losses.
- Multi-platform attacks now hit social media, chat apps, and gaming services.
- Crypto & Web3 scams target wallets with fake dApps or airdrops.
- Zero Trust architectures—never trust, always verify—are the long-term answer.
See our full outlook in Cybersecurity Threats and Trends for 2025. Continuous adaptation is essential in learning how to prevent phishing attacks.
Conclusion
Preventing phishing is all about layered, proactive defense. Pair advanced technical controls—email filtering, MFA, endpoint protection—with a security-aware workforce that pauses before clicking and reports anything suspicious. By combining people, process, and technology, you greatly reduce the chance that a phishing attack will succeed.
Stradiant protects small and midsize organizations across Austin and Central Texas with 24/7 monitoring and custom cyber-security solutions. Whether your office is in Downtown Austin, Bee Cave, Lakeway, Wells Branch, or any of the neighboring communities, we stand ready to help you build a resilient security posture and stay ahead of emerging threats. Ready for stronger defenses? Visit us today!

