Who needs network security?
The simple answer is: everyone.
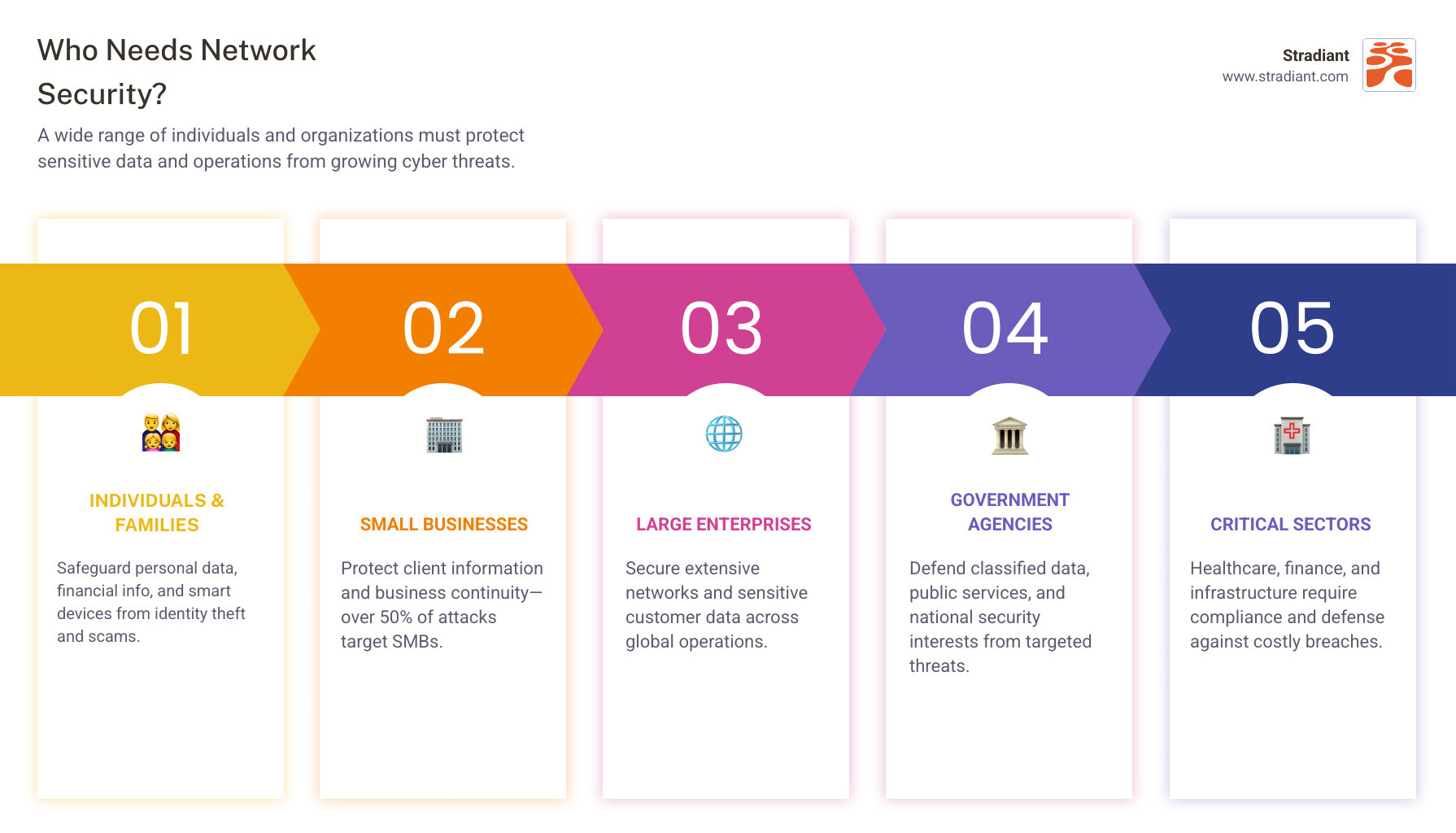
- Individuals and Families: To protect personal data, financial information, and smart home devices.
- Small Businesses and Startups: To safeguard client data, intellectual property, and ensure business continuity.
- Large Enterprises and Corporations: To secure vast networks, sensitive customer data, and maintain global operations.
- Government Agencies: To protect classified information, national security, and essential public services.
- Specific Industries (Healthcare, Finance, etc.): To comply with strict regulations and protect highly sensitive data.
Every day, our lives and businesses become more connected. This brings amazing convenience, but it also creates new risks. Computer security breaches are common, happening around the world every single day. Cybercriminals are getting faster, exploiting new vulnerabilities at an alarming rate.
This isn’t just a problem for big companies. Over 50% of all cyberattacks target small and medium-sized businesses (SMBs). And the cost of a single malware attack can hit over $2.5 million for a company. Neglecting network security can lead to huge financial losses and damage your reputation.
Modern trends like remote work, cloud computing, and the rise of smart devices (IoT) are expanding what needs to be protected. This makes robust network security more vital than ever.
As Joe Dunne, Founder and CEO of Stradiant, I’ve spent years helping organizations, from restaurants to corporations, manage their IT infrastructure and cybersecurity risks. Understanding who needs network security and how to implement it effectively has been central to my work in ensuring businesses can operate securely and confidently.
Similar topics to who needs network security:
The Rising Cost of Breaches

Ever wondered what happens when a company gets hit by a cyberattack? The costs can be truly eye-watering! We’re not just talking about a few dollars here and there. These incidents can wipe out huge sums and cause lasting damage.
Let’s look at some real-world examples:
- Yahoo faced about $350 million in direct costs after a breach affecting 3 billion users. Imagine that price tag!
- Equifax had a massive data breach that cost them over $1.4 billion. That’s with a ‘B’!
- Marriott International also suffered a huge incident in 2020. Information for 5.2 million guests was accessed because employee logins were compromised.
It’s not just the big names that suffer. The average cost of downtime from a cyberattack for any business can reach a staggering $1.58 million per incident. These aren’t just numbers on a spreadsheet. They represent real businesses facing huge financial hits, legal trouble, and damage to their good name. In fact, a 2022 IBM survey found that 83% of companies had more than one data breach. This shows it’s not a rare event but a very real and common threat.
The hidden costs of a breach often sting even more than the immediate ones. Think about:
- Legal penalties and massive regulatory fines if you don’t follow the rules.
- Serious reputational damage that can take years, even decades, to fix. Customers might simply lose trust and take their business elsewhere.
- Lost business because customers are scared to work with you after a breach.
- Your cyber insurance premiums might skyrocket, or your policy could even be canceled.
- Major operational downtime that stops your business dead in its tracks. No work, no income.
What’s truly alarming is how fast cybercriminals are moving. They’re exploiting new weaknesses 43% faster now than just a short while ago. This means businesses have even less time to react and protect themselves.
But here’s the good news: Spending money on strong network security before a breach happens is far, far cheaper than cleaning up the mess afterward. Research tells us that many breaches could have been stopped with just basic security steps. In fact, back in 2014, 44% of breaches came from attacks using weaknesses that were 2-4 years old! This really highlights how preventable many of these costly attacks truly are. It makes you wonder, who needs network security the most? Everyone who wants to avoid these massive costs!
Who Needs Network Security? Everyone from Homes to Critical Infrastructure
When we ask who needs network security, the answer spans every aspect of modern life. Network security isn’t just for tech companies or government agencies – it’s essential for anyone who uses connected devices or stores digital information.
Here’s the reality: if you have a computer, smartphone, or any device connected to the internet, you need network security. The threats are real, and they’re targeting everyone from individual users to critical infrastructure.
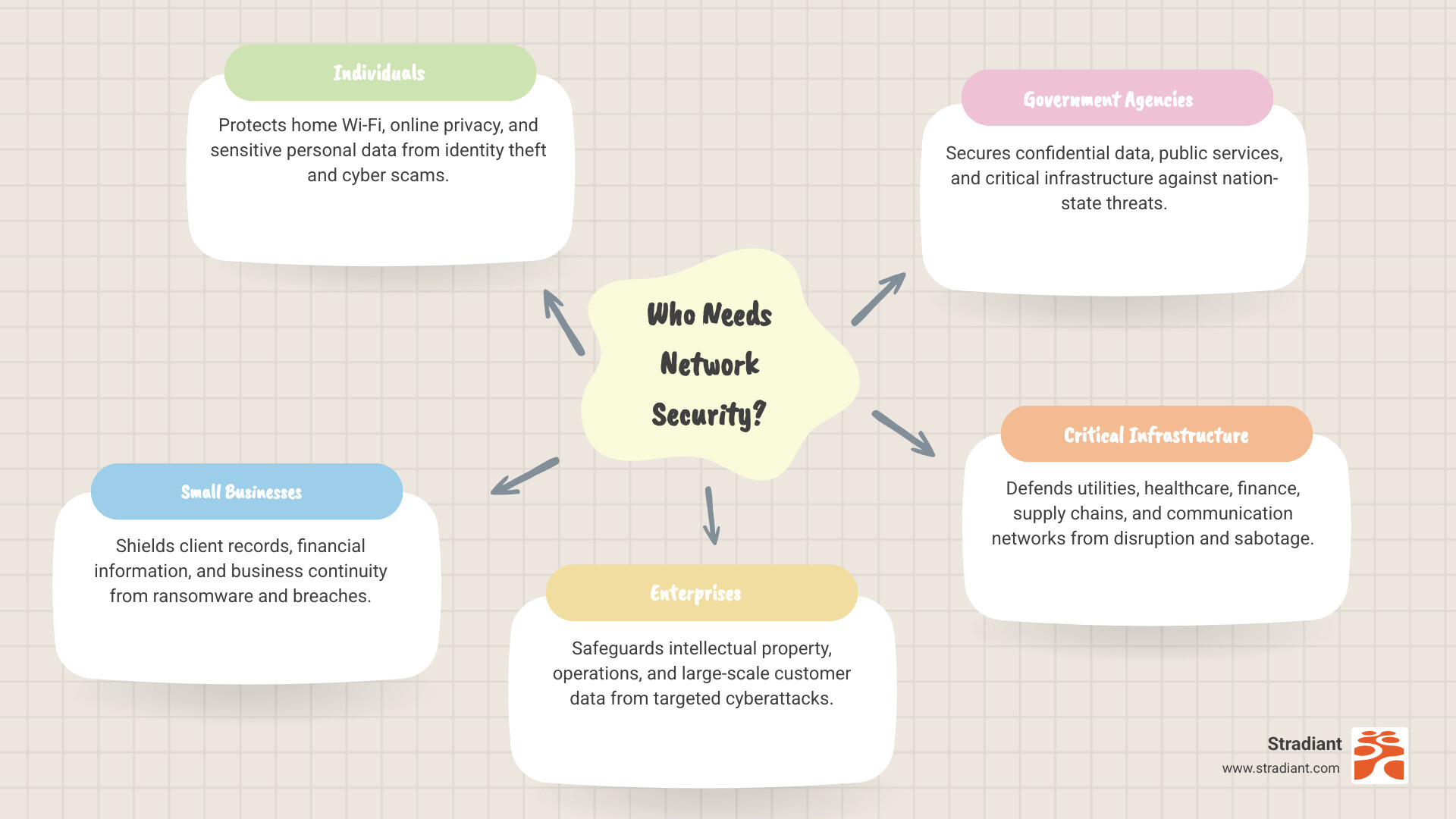
Individuals and families need protection for their personal data, financial information, and increasingly, their smart home devices. A single compromised device can expose your entire home network.
Small and medium-sized businesses are particularly vulnerable. Over 50% of all cyberattacks target SMBs, and 66% of small to medium-sized businesses have experienced a cyber attack in the past 12 months. These businesses often lack dedicated IT security teams, making them attractive targets for cybercriminals.
Large enterprises face sophisticated threats that can compromise vast networks and affect millions of customers. They need comprehensive security strategies that can scale with their operations.
Government agencies must protect classified information and ensure national security. A breach here can have implications far beyond financial losses.
Specific industries like healthcare and finance face strict regulatory requirements (HIPAA, PCI-DSS) and handle extremely sensitive data that makes them high-value targets.
Who Needs Network Security in Personal Life?
Every individual and family with internet-connected devices.
Personal network security protects against:
- Identity theft through compromised personal information
- Financial fraud via stolen banking credentials
- Smart home device hijacking that can compromise your privacy
- Social engineering attacks that trick you into revealing sensitive information
Common personal security measures include:
- Securing home Wi-Fi with WPA3 encryption and strong passwords
- Using VPNs when connecting to public networks
- Keeping devices updated with the latest security patches
- Implementing multi-factor authentication (MFA) on all accounts
- Being aware of phishing attempts and suspicious communications
The rise of remote work has blurred the lines between personal and professional security. When employees work from home, their personal network security directly impacts their employer’s security posture. This makes individual security awareness more critical than ever.
Who Needs Network Security in Business Operations?
Every organization, regardless of size or industry.
The statistics are sobering:
- 50% of all cyberattacks target SMBs
- 66% of SMBs have experienced a cyberattack in the past 12 months
- The average malware attack costs a company over $2.5 million
Businesses need network security to protect:
- Client data and maintain customer trust
- Intellectual property and trade secrets
- Financial information and payment systems
- Operational continuity and avoid costly downtime
- Regulatory compliance and avoid penalties
Modern cyber insurance policies often require specific security measures to qualify for coverage. This means network security isn’t just about protection – it’s becoming a business requirement.
For businesses in Austin and Central Texas, the threat landscape is particularly concerning. As our region continues to grow as a tech hub, cybercriminals are increasingly targeting local businesses. We’ve seen everything from small restaurants to large corporations fall victim to attacks that could have been prevented with proper security measures.
More info about Cybersecurity for Small Businesses
Essential Layers of Modern Network Security
Think of your digital world like a valuable home or office building. You wouldn’t just have one lock on the front door and call it secure, right? You’d have multiple layers: strong doors, window locks, an alarm system, perhaps even security cameras. Modern network security works much the same way. It’s not a single solution, but a powerful, layered defense strategy designed to protect against all sorts of threats.
At the very front lines, we have firewalls. These are your network’s vigilant gatekeepers, constantly watching all traffic trying to enter or leave. They act like a strict bouncer, allowing only the good stuff in and keeping the bad stuff out, based on rules you set. Today’s “next-generation” firewalls are even smarter, able to inspect traffic deeply and block sneaky threats.
Then there’s the concept of Zero Trust Architecture. This might sound a bit harsh, but its motto is simple: “never trust, always verify.” Instead of assuming everyone and everything inside your network is safe, Zero Trust demands that every user and device proves who they are and that they’re authorized, every single time, no matter where they’re trying to connect from. It’s like having a security checkpoint at every internal doorway, not just the main entrance.
To make sure only the right devices are even allowed on your network, we use Network Access Control (NAC). This technology acts like a digital bouncer at the door, checking that any device trying to connect – whether it’s a laptop, a tablet, or a smart printer – is authorized and meets your security standards before it gets access.
And what about your most precious information? That’s where Data Loss Prevention (DLP) comes in. DLP technologies are like watchful guardians, monitoring your sensitive data (think customer lists, financial records, or secret recipes) to make sure it doesn’t accidentally or maliciously leave your network and fall into the wrong hands.
Now, imagine having a highly intelligent security team constantly monitoring every single event happening across your entire network. That’s essentially what Security Information and Event Management (SIEM) systems do. They collect and analyze security data from everywhere, giving you real-time alerts and helping you spot trouble before it becomes a full-blown crisis. Closely related are Intrusion Detection and Prevention Systems (IDS/IPS), which are like watchful eyes and swift hands, scanning network traffic for anything suspicious and automatically blocking threats as soon as they’re detected.
To strengthen your access points, Multi-Factor Authentication (MFA) is a game-changer. It goes beyond just a password, requiring a second (or even third) form of verification – like a code from your phone or a fingerprint – before granting access. It’s like adding a deadbolt to your digital lock.
But even with all these protections, sometimes things happen. That’s why regular backups are absolutely non-negotiable. If ransomware locks up your files, or a system crashes, having up-to-date backups means you can restore your data and get back to business without having to pay criminals or suffer significant downtime. And when an incident does occur, having a clear incident response plan in place ensures your team knows exactly what to do, acting quickly and effectively to contain the damage.
Finally, let’s not forget the human element. The unfortunate truth is that employees can often be the weakest link in security, simply because they might not recognize a trick. That’s why employee training is so vital. Regular awareness programs help staff spot phishing attempts, understand safe online practices, and become an active part of your security defense.
Looking to the future, AI and machine learning analytics are becoming increasingly powerful in the fight against cyber threats. These smart systems can analyze vast amounts of data, learn normal patterns, and quickly spot unusual behaviors that might indicate a sophisticated attack – even ones that traditional security tools might miss.
More info about IT Security Monitoring
Modern Trends Amplifying Risk: Remote Work, Cloud, IoT & 5G

Several key trends are expanding the attack surface and creating new vulnerabilities that businesses must address.
Remote Work Revolution
Remote work has seen 91% growth over the past decade, and this trend accelerated dramatically during the pandemic. While this offers flexibility and cost savings, it also creates significant security challenges:
- Employees connecting from unsecured public Wi-Fi networks
- Personal devices accessing corporate networks
- Increased risk of man-in-the-middle attacks
- Difficulty maintaining consistent security policies across distributed teams
The research shows that 37% of professionals use coffee shops for remote work, and 57% of businesses have no formal work-from-home policies. This creates a perfect storm for security vulnerabilities.
Cloud Computing Expansion
As businesses migrate to cloud platforms, they face new security considerations:
- Shared responsibility models where security is split between cloud providers and customers
- Misconfigurations that can expose sensitive data
- The need for Secure Access Service Edge (SASE) solutions
- Identity and access management challenges across multiple cloud platforms
Internet of Things (IoT) Proliferation
Smart devices are everywhere – from office thermostats to manufacturing sensors. Each connected device represents a potential entry point for attackers:
- Many IoT devices have weak default security settings
- Firmware updates are often neglected
- Network segmentation becomes critical to isolate IoT devices
- Behavioral analytics help detect unusual device behavior
5G Network Deployment
While 5G promises faster speeds and lower latency, it also introduces new attack surfaces:
- Increased number of connection points
- More complex network architecture
- New protocols that may have unfinded vulnerabilities
- Greater potential impact from successful attacks due to increased connectivity
Accelerating Threat Evolution
Cybercriminals are adapting faster than ever. They’re exploiting new vulnerabilities 43% faster than in previous years, and they’re using AI to automate and scale their attacks.
The key to addressing these evolving threats is implementing comprehensive security strategies that can adapt to new challenges. This includes:
- Zero-trust network architectures
- Continuous monitoring and behavioral analytics
- Regular security assessments and updates
- Employee training on emerging threats
More info about Cybersecurity Awareness Training
Frequently Asked Questions about Network Security
What is network security and how does it work?
Network security is like having a comprehensive security system for your digital world. Just as you wouldn’t leave your home or business open uped, you need multiple layers of protection to keep cybercriminals out of your network.
Think of it as a layered defense strategy where each component works together to create a secure environment. Firewalls act as your first line of defense, filtering traffic and deciding what can enter your network based on predetermined rules. Encryption scrambles your data so that even if someone intercepts it, they can’t read it without the proper key.
Access controls ensure only authorized users can reach specific resources – like having different keys for different rooms in a building. Monitoring systems watch for suspicious activity around the clock, while response protocols automatically activate when threats are detected.
The beauty of this approach is that if one security measure fails, others are still protecting your network. It’s redundancy that keeps you safe, and it’s why modern network security is so effective when implemented properly.
How much does network security cost compared to a breach?
Here’s the truth that might surprise you: investing in network security upfront costs a fraction of what you’ll pay after a breach.
The return on investment (ROI) for proper security measures is substantial. Prevention costs typically include security software, employee training, regular assessments, and managed security services. These investments might seem significant initially, but they pale in comparison to breach costs.
Breach averages tell a sobering story. The average malware attack costs a company over $2.5 million. Yahoo spent approximately $350 million dealing with their breach aftermath. These costs include direct remediation expenses, legal fees, regulatory fines, lost business, operational downtime, and increased insurance premiums.
The prevention savings are dramatic. That $350 million Yahoo spent could have funded comprehensive security measures for hundreds of businesses. For small businesses here in Austin and Central Texas, we’ve seen that investing in managed security services costs a fraction of what a single successful attack would cost in downtime, data recovery, and reputation damage.
The math is clear: prevention is always cheaper than cure when it comes to cybersecurity.
What first steps should a small business take today?
If you’re feeling overwhelmed by who needs network security and where to start, take a deep breath. You don’t need to implement everything at once, but you do need to start protecting your business today.
Start with a risk assessment to understand your current vulnerabilities. This gives you a clear picture of what needs immediate attention and what can wait. Implement automated backups of all critical data – this single step can save you from ransomware attacks that cripple businesses.
Deploy basic security measures like firewalls and antivirus software, then train your employees on recognizing phishing attempts and social engineering. Your team is often your strongest defense when they know what to look for.
Keep all software and systems updated regularly. Many successful attacks exploit known vulnerabilities that could have been prevented with timely updates.
Consider partnering with a managed IT provider for 24/7 monitoring and support. This gives you access to enterprise-level security expertise without the cost of hiring a full-time security team.
For businesses throughout Central Texas, we recommend starting with a comprehensive security assessment to understand your specific risks and create a custom protection strategy. The key is to start with the basics and build from there – but start today.
Conclusion & Next Steps
Network security isn’t optional – it’s essential for everyone from individuals protecting their personal information to businesses safeguarding their operations and customers’ data. The question isn’t who needs network security, but rather how quickly you can implement effective protection.
The statistics paint a clear picture: cyberattacks are increasing in frequency and sophistication, with over 50% targeting small and medium-sized businesses. The cost of a single breach can reach millions of dollars, while the investment in proper security measures costs significantly less. We’ve seen how companies like Yahoo spent $350 million on breach costs – money that could have funded comprehensive security for countless businesses.
Every day you delay implementing proper network security is another day your business remains vulnerable to attack. The threats are real, but so are the solutions.
24/7 monitoring has become essential in today’s threat landscape. Cybercriminals don’t work business hours, and neither should your security defenses. Having expert support available around the clock means threats can be detected and neutralized before they cause damage.
The businesses that thrive in our increasingly connected world are those that prioritize security from the start and continuously adapt their defenses to meet evolving threats. They understand that custom security strategies aren’t just nice to have – they’re business necessities.
Businesses face unique challenges as our region continues to grow as a tech hub. Cybercriminals are increasingly targeting local businesses, from small restaurants to large corporations. The good news is that with proper planning and implementation, these threats can be effectively managed.
Risk mitigation starts with understanding your specific vulnerabilities and implementing layered defenses that grow with your business. This includes everything from basic firewalls and backups to advanced threat detection and employee training programs.
Don’t wait for a breach to realize the importance of network security. The businesses that succeed are those that view security as an investment in their future, not just an expense. With the right approach, you can protect your operations, your data, and your reputation while focusing on what you do best.
Ready to secure your business? The solutions are available, and the time to implement them is now. Your business can’t afford to ignore network security – but with proper planning and expert guidance, you can implement it effectively and affordably.
More info about Managed IT: Securing Your Network

