A cyber security risk assessment is a systematic process that identifies, analyzes, and evaluates potential security threats to an organization’s information systems and data assets. For business leaders seeking immediate guidance, here’s what you need to know:
| Cyber Security Risk Assessment: Key Components |
|---|
| 1. Identify valuable assets (hardware, software, data) |
| 2. Catalog threats and vulnerabilities to those assets |
| 3. Assess likelihood and potential impact of security events |
| 4. Calculate risk levels based on threat, vulnerability, and impact |
| 5. Implement appropriate security controls to mitigate identified risks |
| 6. Document and monitor results continuously |
The growing sophistication of cyber threats has made regular risk assessments essential for businesses of all sizes. With the global average cost of a data breach reaching $4.88 million in 2023, organizations cannot afford to take a reactive approach to cybersecurity.
Without a proper assessment, you’re essentially operating in the dark, unaware of where your most significant vulnerabilities lie or how to address them effectively. This is particularly concerning for small and medium-sized businesses, which often lack dedicated IT security teams but remain attractive targets for cybercriminals.
My name is Joe Dunne, founder and CEO of Stradiant, and I’ve helped numerous organizations conduct comprehensive cyber security risk assessments to protect their critical assets and ensure business continuity. My experience as an IT Director and consultant has shown me how proper risk assessment forms the foundation of any effective cybersecurity strategy.
What Is a Cyber Security Risk Assessment?
Think of a cyber security risk assessment as a comprehensive health check-up for your IT. It’s the process where we systematically examine your IT environment to spot vulnerabilities before the bad guys do.
In plain language, we’re looking for the weak spots in your digital armor and figuring out how likely they are to be exploited—and what damage that might cause.
NIST (the National Institute of Standards and Technology) defines it as “the process of identifying, estimating, and prioritizing information security risks.” But what does that really mean for your business?
A thorough assessment examines four critical elements:
- Threats – These are the dangers lurking out there: ransomware, phishing attacks, disgruntled employees, or even natural disasters that could affect your technology
- Vulnerabilities – The weak points in your systems: outdated software, poor password practices, or lack of encryption
- Impact – What happens if something goes wrong? Data loss? Operational downtime? Damage to your reputation?
- Likelihood – How probable is it that a specific threat will successfully exploit a vulnerability?
When we combine likelihood with impact, we get a clear picture of your overall risk level—the foundation for smart security decisions.
Several respected frameworks guide how we conduct these assessments, including NIST SP 800-30, ISO 27001, and CIS RAM (Risk Assessment Method). Each offers structured approaches to identifying and managing cybersecurity risks.
According to the National Vulnerability Database, thousands of new vulnerabilities emerge each year. Without regular assessments, these hidden dangers can go undetected until it’s too late.
Cyber Security Risk Assessment vs. General Risk Assessment
While general business risk assessments cast a wide net—looking at financial risks, market conditions, and operational concerns—a cyber security risk assessment has a more focused mission.
Cyber assessments specifically examine what we call the CIA triad: the Confidentiality, Integrity, and Availability of your information assets. We’re looking exclusively at your digital field: the systems, data, networks, and people that interact with them.
A general risk assessment might worry about physical building security or economic downturns. Our cyber security risk assessment zeroes in on protecting your digital crown jewels from the constantly evolving threat landscape.
Key Terminology Cheat-Sheet
When we talk about risk assessments, these are the terms you’ll want to understand:
Risk Appetite – How much risk your organization is comfortable accepting. Some businesses are conservative, others more risk-tolerant.
Inherent Risk – This is your “raw” risk level before any security controls are applied—your baseline vulnerability.
Residual Risk – After implementing security measures, this is the risk that remains. It should align with your risk appetite.
Asset Criticality – Not all systems are created equal. This measures how essential a particular asset is to your core operations.
Crown Jewels – Your most valuable digital assets—the data and systems that absolutely must be protected at all costs.
Attack Surface – All the potential entry points where hackers could attempt to breach your systems—from email to web applications to remote access points.

Understanding these concepts helps you speak the language of risk and make more informed decisions about your security investments. At Stradiant, we translate these technical concepts into practical, business-focused guidance that makes sense for your organization.
Why Regular Cyber Security Risk Assessments Matter
Cyber security assessments aren’t just a nice-to-have—they’re essential for your business’s survival and success. Think of them as regular health check-ups for your digital infrastructure, helping you stay ahead of threats before they become costly problems.
The stakes have never been higher. With the average data breach now costing companies a staggering $4.88 million, prevention isn’t just cheaper than cure—it’s crucial for staying in business. But the benefits go far beyond just avoiding financial loss.
Regulatory compliance requirements continue to tighten across industries. Whether it’s GDPR, HIPAA, or PCI DSS, most regulations now mandate regular security assessments. By staying on top of these requirements, you avoid potential fines while building trust with your stakeholders—customers, partners, and investors who increasingly expect robust security measures.
Business continuity is another critical factor. When you identify and address vulnerabilities proactively, you prevent the operational disruptions that can damage your reputation and bottom line. This becomes even more important as new technologies enter your environment.
Speaking of new tech, emerging technologies like generative AI are creating fresh security challenges. Research shows only 24% of AI initiatives are properly secured, opening new attack vectors for cybercriminals. Meanwhile, ransomware attacks continue their upward trend, with the average recovery cost now reaching $2 million per incident.
The World Economic Forum’s Global Cybersecurity Outlook 2025 report paints a sobering picture: we’re entering an era of unprecedented complexity in cybersecurity, driven by intensifying geopolitical tensions, rapid technological change, and increasingly sophisticated threat actors.
For more insights into what’s coming next in cybersecurity, check out our article on Cybersecurity Threats and Trends for 2025.
Benefits for SMBs & Public Safety Centers
Small and medium-sized businesses and public safety organizations face unique security challenges but stand to gain tremendous benefits from regular cyber security risk assessments.
For SMBs, downtime can be devastating. Regular assessments help prevent outages that larger organizations might weather but could put smaller companies out of business. With typically limited security budgets, SMBs also benefit from optimized resource allocation based on actual risk data rather than assumptions.
Public safety centers have their own critical concerns. When you’re responsible for emergency services, ensuring 24/7 availability isn’t just a business goal—it’s a public safety imperative.
Both SMBs and public safety organizations can leverage resources from the Cybersecurity and Infrastructure Security Agency (CISA), including their Cyber Security Evaluation Tool (CSET®). This free resource provides a systematic approach to evaluating your security posture, even with limited internal expertise.
Perhaps most importantly for small businesses, these assessments help protect your hard-earned reputation. In local communities especially, trust is everything—and a preventable security breach can damage that trust irreparably.
Frameworks & Methodologies at a Glance
When conducting your cyber security risk assessment, several established frameworks can guide your process:
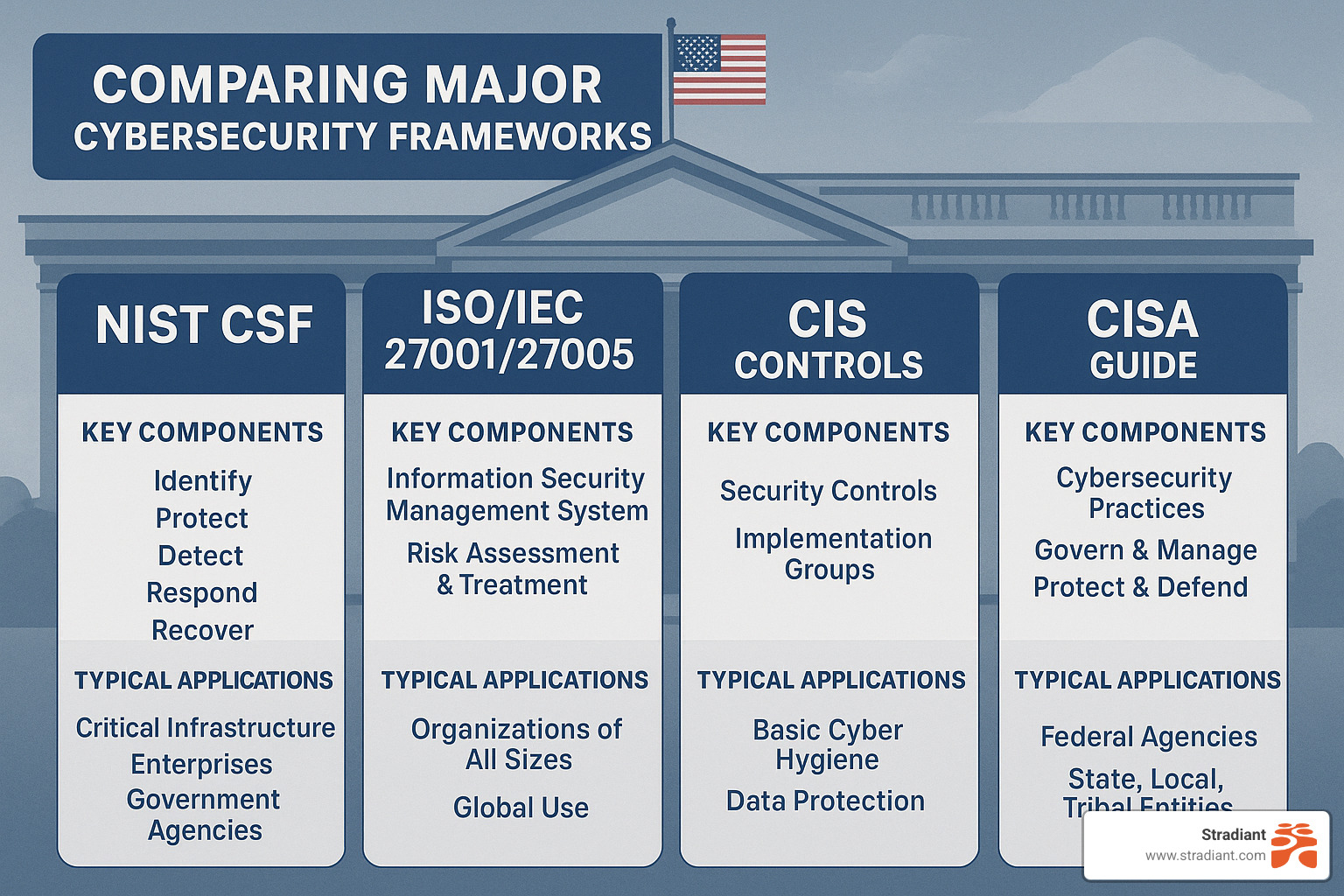
NIST CSF 2.0 offers a comprehensive approach with six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. This framework works well for organizations seeking a thorough methodology that addresses the full security lifecycle.
ISO 27001/27005 takes a process-oriented approach integrated with broader information security management systems. International businesses often prefer this framework, especially when seeking certification that demonstrates compliance to global partners.
CIS Controls provides practical implementation guidance with a prioritized set of actions to protect against known attack vectors. This framework is particularly helpful for organizations that need clear, actionable steps.
CISA Guide is custom-designed for critical infrastructure and emergency services, making it ideal for public safety organizations and government entities with specialized security needs.
Many of our clients at Stradiant find that combining elements from multiple frameworks works best for their specific situation. The right approach depends on your industry, size, and particular risk factors—there’s no one-size-fits-all solution when it comes to protecting your digital assets.
Step-by-Step Cyber Security Risk Assessment Framework
When it comes to protecting your business, having a clear roadmap makes all the difference. A successful cyber security risk assessment isn’t a one-time event but rather a journey that follows a structured, repeatable process. Think of it as your organization’s security compass—guiding you through potential dangers while keeping your valuable assets safe.
I’ve found that the most effective assessments balance both qualitative measures (expert judgments) and quantitative data (measurable metrics) to give you the complete picture of your security landscape. This balanced approach ensures you’re making decisions based on both hard numbers and contextual understanding.
What makes a truly valuable assessment isn’t just identifying today’s risks—it’s establishing a continuous monitoring system that keeps you ahead of tomorrow’s threats. The security landscape changes rapidly, and your assessment process needs to evolve just as quickly.
While different frameworks may have their own specific approaches, the methodology I’m about to share works wonderfully for organizations of all sizes, from small Austin businesses to larger enterprises. The beauty of this framework is its adaptability—you can customize it to fit your specific industry needs while maintaining the core structure that makes it effective.
Let’s walk through each step of this journey together, breaking down what might seem like an overwhelming process into manageable, actionable steps that will strengthen your security posture over time.
1. Define Scope & Context
The foundation of any effective cyber security risk assessment begins with clearly defining your boundaries. Think of this step as drawing a map before starting on a journey—you need to know exactly where you’re going and what terrain you’ll cover.
When we work with businesses, we always start by having a conversation about what matters most to them. This helps us focus our efforts where they’ll have the greatest impact.
Your scope definition should address these key elements:
Business Processes that will be included in your assessment deserve careful consideration. Are you looking at your entire operation, or focusing on specific departments like accounting, customer service, or product development? Each process has its own unique security considerations.
System Boundaries establish exactly which digital assets fall within your assessment. This includes networks, servers, applications, databases, and even cloud services. Being specific here prevents both gaps in coverage and wasted effort.
Risk Tolerance varies significantly between organizations. A financial institution might have near-zero tolerance for certain risks, while a small retail business might accept more risk in some areas. Defining your comfort level upfront helps prioritize your response strategy.
Legal and Regulatory Requirements create a baseline for your assessment. Depending on your industry, you might need to address specific frameworks like HIPAA for healthcare, PCI DSS for payment processing, or various state data protection laws.
Document these parameters clearly so everyone involved shares the same understanding of the assessment’s scope. This documentation becomes your roadmap for the entire process and helps prevent scope creep.
Many organizations make the mistake of trying to assess everything at once, which can quickly become overwhelming. Instead, consider starting with your most business-critical systems or those containing sensitive data, then expanding your assessment to other areas in subsequent cycles.
For example, if you’re a medical practice in Austin, you might begin by focusing on your patient records system due to both HIPAA requirements and the sensitive nature of the data. A retail business might prioritize point-of-sale systems and customer databases.
A well-defined scope isn’t just about limiting your work—it’s about ensuring you’re directing your security efforts where they matter most.
2. Identify & Prioritize Assets
You can’t protect what you don’t know exists in your organization. This crucial step of your cyber security risk assessment is all about taking inventory and understanding what matters most.
Think of this as creating a detailed map of your digital kingdom. We need to know what treasures you have before we can build the right walls around them.
Start by creating a comprehensive asset inventory that includes all hardware (servers, workstations, mobile devices), software applications, data repositories, and network systems within your defined scope. This foundation gives you visibility into your entire digital ecosystem.
Next comes the important work of data classification. Not all information carries equal weight. Customer financial data deserves stronger protections than your company lunch menu. Categorize your information based on sensitivity and business value, using simple classifications like Public, Internal, Confidential, and Restricted.
Identifying your crown jewels is perhaps the most critical part of this phase. These are the assets that would cause severe damage to your business if compromised. For most organizations, these include:
- Customer databases and personal information
- Financial records and payment processing systems
- Proprietary intellectual property and trade secrets
- Authentication systems and access credentials
- Business-critical operational systems
Understanding how these systems connect is equally important. Dependency mapping reveals how your assets interconnect, showing which systems rely on others to function. This helps identify hidden vulnerabilities where a compromise in one system could cascade throughout your organization.
Finally, assign value ratings to prioritize your assets. Consider factors like:
| Consideration | Questions to Ask |
|---|---|
| Business Impact | What happens if this asset is compromised? |
| Regulatory Requirements | What compliance obligations apply to this asset? |
| Recovery Complexity | How difficult would it be to restore this asset? |
| Replacement Cost | What would it cost to replace this asset? |
This prioritization ensures you focus your limited security resources where they’ll have the greatest impact. At Stradiant, we’ve seen many organizations find previously unknown critical assets during this process, highlighting why this step is so valuable.
This isn’t a one-time task. Your asset inventory should be regularly updated as your business evolves, new systems come online, and others are retired. The digital landscape is always changing, and your asset inventory needs to keep pace.
3. Find Threats & Vulnerabilities
Now that you’ve mapped out what you’re protecting, it’s time to identify what you’re protecting it from. This detective work is crucial to your cyber security risk assessment – you need to know both the threats targeting your assets and the vulnerabilities those threats might exploit.
Think of threats as the “who” or “what” that might harm your systems, while vulnerabilities are the “how” – the weaknesses that make attacks possible.
Understanding Your Threat Landscape
Threats to your business can come from surprising places. While we often picture shadowy hackers, the reality is more diverse:
- External threats from cybercriminals, hacktivists, or even nation-states
- Internal risks from disgruntled employees or accidental actions
- Environmental factors like power outages or natural disasters
- Technical failures in systems or software
To stay ahead of these threats, tap into reliable intelligence sources. The MITRE ATT&CK framework has become the gold standard, offering a detailed knowledge base of adversary tactics and techniques based on real-world observations. It’s like having a playbook of how attackers operate.
Many of our clients find the STRIDE model particularly helpful for thinking about different threat categories: Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege.
Uncovering Your Vulnerabilities
Vulnerabilities are the cracks in your armor – the weak points that threats can exploit. Finding them requires both technical tools and human expertise.
At Stradiant, we use a multi-layered approach to vulnerability findy:
Automated scanning can quickly identify known technical weaknesses, like missing patches or misconfigured systems. These tools are excellent for establishing a baseline, but they’re just the beginning.
Penetration testing takes vulnerability assessment to the next level. Our ethical hackers attempt to exploit weaknesses just as real attackers would, revealing vulnerabilities that automated tools might miss.
Configuration analysis examines how your systems are set up, looking for security gaps in settings that might seem harmless but create serious risks.
Human factor assessment recognizes that people are often the weakest link. We evaluate susceptibility to social engineering and phishing through safe simulations and awareness checks.
The most common vulnerabilities we find in SMBs include unpatched software, weak passwords, excessive user privileges, lack of encryption, and insufficient backup procedures. Each represents an open door for attackers.
For each critical asset you identified in the previous step, document both the relevant threats and the vulnerabilities that might allow those threats to succeed. This creates a comprehensive risk profile that will guide your next steps.
Finding vulnerabilities isn’t about placing blame – it’s about identifying opportunities to strengthen your defenses before attackers can exploit them. As we like to tell our clients: in cybersecurity, what you don’t know absolutely can hurt you.
4. Calculate & Prioritize Risk in a Cyber Security Risk Assessment
Now comes the moment of truth – figuring out just how worried you should be about each risk you’ve identified. Think of this step as sorting your security concerns from “keep you up at night” to “worth keeping an eye on.”
We find that making risk tangible helps leaders make better decisions about where to invest their security dollars. After all, you can’t fix everything at once, so knowing what matters most is crucial.
Risk Calculation Methods
Most organizations take one of two approaches to measuring risk:
- Qualitative Assessment: This uses descriptive categories like “High,” “Medium,” and “Low” for both likelihood and impact. It’s straightforward and often sufficient for smaller organizations just beginning their security journey.
- Quantitative Assessment: This method assigns actual numbers to your risks, using formulas such as:
- Risk = Likelihood × Impact
- Annual Loss Expectancy (ALE) = Single Loss Expectancy (SLE) × Annual Rate of Occurrence (ARO)
For organizations wanting more precision, the FAIR (Factor Analysis of Information Risk) model breaks down risk components into detailed factors that can be measured more objectively. This approach works well for businesses that need to justify security investments to boards or leadership teams.
Risk Matrix
Nothing communicates risk quite like a visual. A risk matrix helps you see at a glance which risks need immediate attention:

The beauty of this heat map approach is its clarity – red zones demand immediate action, while yellow and green areas might be addressed later or accepted as part of your risk appetite.
Embracing Uncertainty
Let’s be honest – cyber security risk assessment isn’t an exact science. There’s always uncertainty involved. That’s why we recommend expressing risk with ranges rather than precise values:
“There is an 80% ±10% chance of a ransomware attack in the next 12–24 months, with a potential cost impact of $1–2M if systems are held hostage.”
This approach acknowledges the reality of uncertainty while still providing actionable information.
Smart Prioritization
Once you’ve calculated your risks, it’s time to decide which ones deserve your attention first. Consider these factors when prioritizing:
Overall risk score helps you focus on the biggest threats first. Asset criticality ensures you’re protecting what matters most to your business. Mitigation feasibility addresses the practical reality of what you can actually fix with available resources. And regulatory requirements keep you on the right side of compliance obligations.
The goal isn’t to eliminate all risk (that’s impossible) but to bring risks down to a level your organization can accept and manage.
Risk calculation isn’t a one-time event. As your business and the threat landscape evolve, so too will your risk profile. Regular reassessment ensures you’re always focusing your security efforts where they’ll have the greatest impact.
5. Select & Implement Security Controls
Now that you’ve mapped out your risks, it’s time for the action phase – selecting and implementing the right security controls to protect your business. Think of this as building your digital fortress, with each control serving as a specific defense mechanism.
Security controls aren’t one-size-fits-all. The right mix for your organization will depend on your unique risk profile, budget constraints, and operational needs. Let’s explore your options:
Different controls serve different purposes in your security ecosystem. Preventive controls act as your first line of defense, stopping threats before they can cause harm – like sturdy locks on your doors. Detective controls are your security cameras, alerting you when something suspicious happens. Corrective controls help you recover after an incident, like having a good insurance policy. And compensating controls provide alternatives when your primary defenses aren’t feasible.
We often recommend a balanced approach that includes several layers of protection:
Multi-factor authentication (MFA) has become non-negotiable in today’s threat landscape. By requiring something you know (password) and something you have (like your phone), MFA can prevent up to 99.9% of account compromise attacks. It’s one of the most cost-effective controls you can implement.
Data encryption protects your information both when it’s stored (at rest) and when it’s being transmitted (in transit). Even if attackers gain access to your systems, properly encrypted data remains unreadable and unusable to them.
Regular patch management addresses vulnerabilities before attackers can exploit them. Think of unpatched systems as open uped windows in your building – easy entry points for intruders.
Security awareness training transforms your team from a potential vulnerability into a human firewall. Your security is only as strong as your least security-conscious employee.
When selecting which controls to implement first, consider:
- Which risks pose the greatest threat to your critical assets?
- What’s the implementation cost versus the potential loss you’re preventing?
- How will the control impact your daily operations?
- Are there regulatory requirements you must satisfy?
The best approach is usually to start with addressing your highest risks first, then work your way down the list. Don’t try to implement everything at once – that’s a recipe for overwhelm and poor execution. Instead, develop a phased implementation plan with clear timelines and responsibilities.
Security is never “done.” As your business evolves and new threats emerge, you’ll need to continuously evaluate and adjust your controls. For more guidance on implementing effective security measures, check out our resource on How to Mitigate Cyber Risk.
A cyber security risk assessment isn’t just about finding problems – it’s about solving them with the right mix of controls that protect your business without breaking your budget or hampering your operations.
6. Document, Communicate & Monitor Results of Your Cyber Security Risk Assessment
The final step might seem like paperwork, but it’s actually where all your hard work becomes truly valuable. Documenting, sharing, and continuously monitoring your cyber security risk assessment results transforms your one-time effort into an ongoing shield for your business.
Creating a Living Document
Think of your documentation as the storybook of your security journey. Your risk register becomes the central character – a comprehensive inventory that tracks each identified risk, its severity rating, and your plans to address it. This isn’t just for compliance checkboxes; it’s your roadmap for protecting what matters most.
Beyond the risk register, you’ll want to maintain:
- A detailed catalog of your security controls (what’s working and what isn’t)
- Clear records of your assessment methodology (so you can repeat and improve)
- Evidence of your testing and scanning activities (your proof of diligence)
The best documentation strikes a balance – thorough enough to be useful but organized enough that you’ll actually reference it when needed.
Speaking Everyone’s Language
Not everyone needs (or wants) the same level of detail. The key is tailoring your message to different audiences:
Your executive team needs the headline version – what are our biggest risks, what’s it going to cost, and how does this impact our business goals? Use visuals like heat maps to show risk concentration at a glance.
Your IT team needs the technical details – specific vulnerabilities, required patches, and implementation timelines. Give them actionable items with clear ownership.
Department managers need to understand how security relates to their specific operations. When explaining findings to non-technical staff, skip the jargon and focus on practical impacts: “This means you’ll need to change passwords every 90 days” rather than “We’re implementing improved authentication protocols.”
Making Security a Continuous Journey
Your risk assessment isn’t a one-and-done project – it’s the beginning of an ongoing process. The threat landscape evolves daily, and your security posture needs to keep pace.
Set up dashboards to track your security metrics over time. Are your controls actually reducing risk? Are new vulnerabilities being addressed promptly? Regular reviews of your risk register (quarterly at minimum) help ensure nothing falls through the cracks.
Be particularly vigilant when changes occur in your business. New systems, restructured departments, or updated regulations all warrant a fresh look at your risk profile. Many successful organizations implement automated scanning tools that continuously monitor for new vulnerabilities, giving you early warning before problems escalate.
Make it a habit to revisit your assessment after any security incident, too. What worked in your response? What could have been prevented? These insights are gold for strengthening your defenses.
The most successful organizations don’t view their cyber security risk assessment as a burdensome requirement – they see it as their competitive advantage. When you know your risks better than anyone else, you can protect your business with confidence while competitors remain vulnerable to threats they haven’t even identified.
Frequently Asked Questions about Cyber Security Risk Assessment
How often should our organization perform a cyber security risk assessment?
Figuring out how often to run a cyber security risk assessment is a bit like deciding how often to get your car serviced – it depends on what you’re driving and how you use it!
For most organizations, an annual comprehensive assessment makes good sense as a baseline. This gives you a regular checkpoint to measure your security posture and make adjustments.
That said, several factors might push you toward more frequent assessments:
Regulatory requirements might dictate specific schedules depending on your industry. Healthcare organizations under HIPAA or financial institutions under GLBA often face stricter assessment timelines.
Rate of change in your IT environment matters too. If you’re constantly deploying new systems, migrating to the cloud, or undergoing digital change, you’ll want more frequent check-ins on your security posture.
The threat landscape facing your industry should also influence your schedule. Organizations in frequently targeted sectors like finance or critical infrastructure benefit from more regular assessments.
Beyond your annual comprehensive review, I recommend conducting targeted assessments whenever significant changes occur – like implementing a new ERP system, opening a new location, or after a major security incident in your industry.
Which frameworks are best for small-to-medium businesses?
When it comes to choosing a framework, smaller organizations often feel like they’re trying to fit into clothes made for someone else. The good news is that several frameworks can be custom to fit just right!
The NIST Cybersecurity Framework (CSF) works wonderfully for SMBs despite its comprehensive nature. Think of it as a wardrobe you can build over time – start with the essentials (Identify, Protect, Detect, Respond, Recover) and gradually add more sophisticated elements as you grow.
For businesses just getting started with formal security programs, the CIS Controls are particularly friendly. They’re organized into “Implementation Groups” that help you prioritize what to tackle first based on your size and resources. It’s like having a roadmap that says, “Start here if you’re small, then add these controls as you mature.”
CISA’s Cyber Resilience Review (CRR) also deserves consideration. It’s designed to be accessible regardless of your organization’s size and provides a solid foundation for building your security program.
The perfect framework is the one you’ll actually use. Start simple, focus on protecting your crown jewels, and build your program incrementally as your resources and maturity allow.
How is risk actually calculated and visualized for decision-makers?
Translating complex security concepts into something business leaders can use to make decisions is perhaps the trickiest part of a risk assessment. Here’s how we make that magic happen:
Most organizations use one of three approaches, depending on their maturity and needs:
The Simple Qualitative Matrix is the most straightforward approach. We assign ratings like High, Medium, or Low to both the likelihood of something bad happening and the impact if it does. Then we plot these on a grid (usually 3×3 or 5×5) and color-code the results – red for critical risks, yellow for moderate concerns, and green for lower priorities. This visual approach makes it immediately clear where attention is needed.
For more precision, many organizations use a Semi-Quantitative Scoring system. This assigns numbers (typically 1-5) to likelihood and impact, then multiplies them together for a risk score between 1-25. A score of 20-25 might be categorized as “Critical Risk,” while 1-5 might be “Low Risk.” This approach gives you more granularity without requiring complex calculations.
Organizations with more mature risk programs often employ Quantitative Analysis, expressing risk in financial terms. For example: “This vulnerability creates a potential annual loss of $50,000.” To account for uncertainty, we typically present ranges rather than precise figures: “We estimate the potential impact between $40,000-$60,000.”

When communicating with executives, the secret sauce is connecting security risks to business outcomes they care about. Instead of talking about “unpatched vulnerabilities,” frame it as “potential business disruption that could cost $X in lost revenue.” Use clear visualizations like heat maps or bar charts showing risks ranked by potential financial impact.
The goal isn’t just to calculate risk accurately – it’s to present it in a way that enables informed business decisions about where to invest your limited security resources.
Conclusion
Implementing a robust cyber security risk assessment process is no longer optional for businesses of any size—it’s a fundamental component of responsible business management. As we’ve explored throughout this guide, these assessments provide the foundation for effective security decision-making, resource allocation, and risk management.
The six-step framework we’ve outlined—defining scope, identifying assets, finding threats and vulnerabilities, calculating risk, implementing controls, and monitoring results—provides a structured approach that any organization can adapt to its specific needs and resources.
Cyber security risk assessment is not a one-time project but an ongoing process. The threat landscape evolves constantly, as do your business operations and IT environment. Regular assessments help ensure your security measures remain effective in the face of these changes.
For small and medium-sized businesses in Austin and throughout Central Texas, the stakes are particularly high. Without the extensive resources of larger enterprises, SMBs must be strategic about their security investments, focusing on the controls that address their most significant risks.
Don’t wait for a breach to occur before taking action. Proactive risk assessment is far less costly than breach recovery, both financially and reputationally.
Remember: A thorough cyber security risk assessment is your first step toward achieving these critical business objectives.

