Why Small Businesses Are Prime Targets for Cyberattacks
Cybersecurity for small businesses is no longer optional—it’s essential for survival today. With limited resources and often minimal IT expertise, small businesses have become the preferred targets for cybercriminals.
Quick Guide: Cybersecurity Essentials for Small Businesses
- Train employees on security awareness and phishing recognition
- Use strong passwords and enable multi-factor authentication
- Keep software updated with the latest security patches
- Install antivirus/anti-malware on all devices
- Back up data regularly to secure, off-site locations
- Secure your Wi-Fi network with encryption and hidden SSID
- Implement firewalls for network protection
- Create an incident response plan for when breaches occur
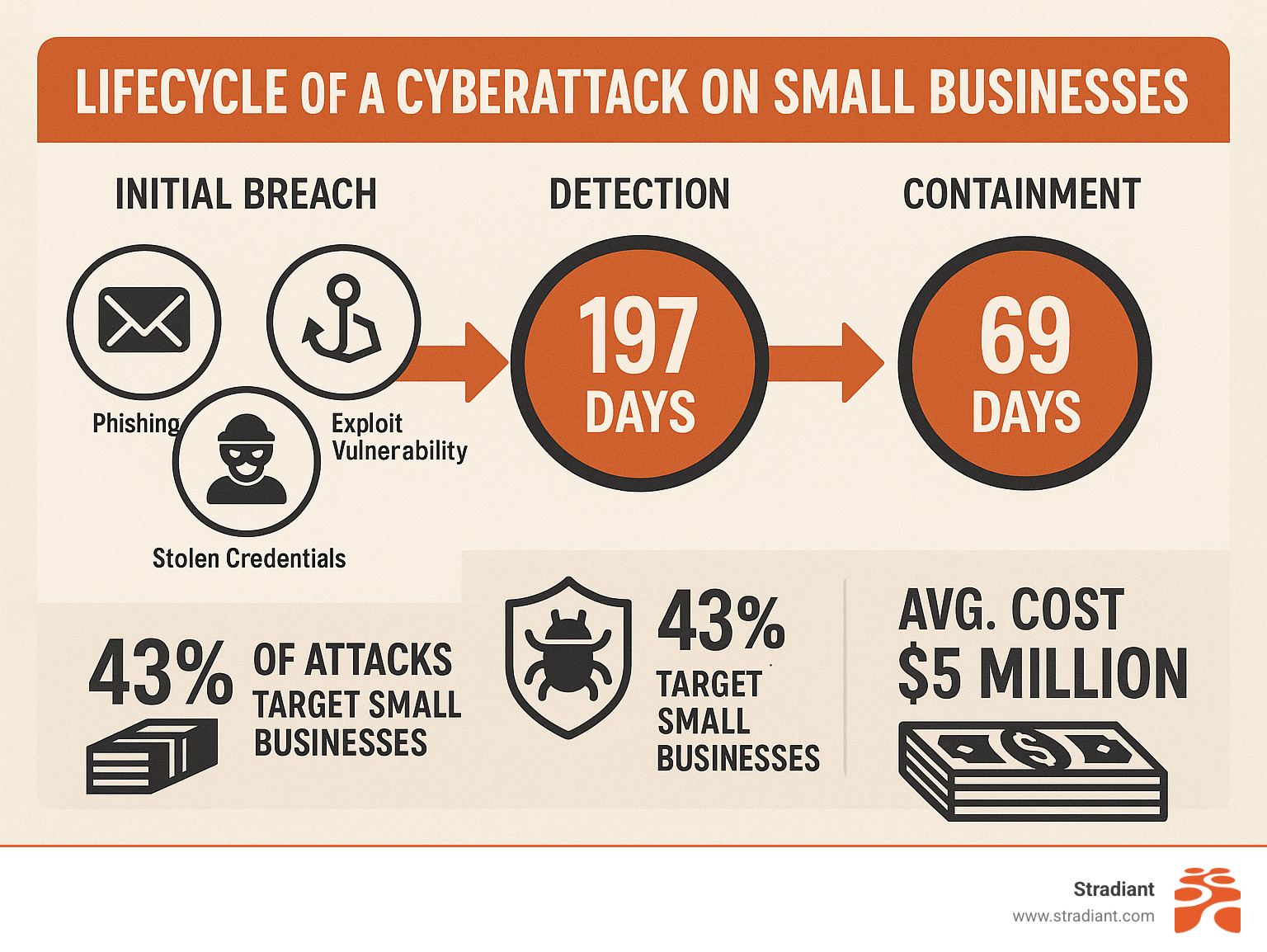
The statistics are alarming: over 43% of cyberattacks specifically target small businesses, and 73% of small and mid-sized businesses experienced a data breach or cyberattack in 2023 alone. Nearly one in five small businesses that suffered a cyberattack filed for bankruptcy or closed entirely.
Why are small businesses such attractive targets? Cybercriminals know that most small companies lack robust security measures while still possessing valuable data. They’re betting on finding easy entry points through outdated software, weak passwords, or untrained employees.
The financial impact can be devastating. The average cost of a cyberattack on a small business can reach $5 million when accounting for downtime, recovery expenses, and reputational damage. Yet despite these risks, only 23% of small business owners report being very satisfied with their cybersecurity prevention plan.
I’m Joe Dunne, founder and CEO of Stradiant, and I’ve spent years helping small businesses in Austin and beyond develop effective cybersecurity strategies that balance protection with practical budget constraints.
Why Cybersecurity for Small Businesses Can’t Wait
Small businesses have gained incredible opportunities in our digital age, but with these opportunities come serious risks. Many business owners believe they’re too small to attract cybercriminals’ attention—a dangerous misconception that often leads to devastating consequences.
The truth is, cybersecurity isn’t something you can put off until tomorrow. The impacts of ignoring proper protection touch every aspect of your business:
The Real-World Costs of a Breach
When cybercriminals strike, the damage goes far beyond what most business owners anticipate. That average $5 million cost for a ransomware attack? It’s just the beginning of a painful journey.
Immediate financial drain hits you first—paying ransoms (if you choose that route), bringing in emergency IT help, and rebuilding systems all require significant cash outlays. Meanwhile, your business grinds to a halt during the operational downtime, which averages 9.6 days after ransomware attacks.
The recovery process brings its own expenses. Rebuilding databases and recovering lost information can be painstaking and costly. Then there’s the legal side—potential lawsuits from affected customers and regulatory penalties for data protection violations can add significant financial burden.
Don’t forget about insurance. After a breach, your cyber insurance premiums will almost certainly increase, assuming your provider doesn’t drop you entirely. And perhaps most devastating is the long-term reputation damage. About 80% of small businesses report spending significant time rebuilding customer trust after an attack.
What’s particularly concerning is the detection gap. Organizations typically take 197 days just to find they’ve been breached, followed by another 69 days to contain the damage.
| Expense Category | Average Cost for Small Business | Cost of Prevention Measures |
|---|---|---|
| Ransomware Payment | $170,000 | $5,000/year (security software) |
| Business Downtime | $8,500 per day | $2,500/year (backup solutions) |
| Data Recovery | $50,000+ | $3,000/year (managed security) |
| Customer Notification | $10,000 | Included in managed services |
| Legal Fees | $20,000+ | $1,500 (incident response planning) |
| Reputation Management | $15,000+ | Included in managed services |
As you can see, prevention isn’t just smarter—it’s dramatically more affordable. Investing in cybersecurity costs a fraction of what you’ll spend recovering from an attack.
The Cyber Threats You’re Up Against
Let’s talk about what you’re really facing today. As a small business owner, understanding these threats is like knowing what symptoms to watch for to keep your business healthy.
Think of malware as the common cold of the cyber world – it’s everywhere, constantly evolving, and designed to infect your systems when you least expect it. Its more dangerous cousin, ransomware, works like a digital kidnapper, locking away your precious data and demanding payment for its return.
Phishing has become increasingly sophisticated – no longer just obvious scam emails with spelling errors. Today’s phishing attempts often look remarkably legitimate, designed to trick even careful employees into giving up credentials or clicking malicious links.

Business Email Compromise attacks are particularly sneaky – imagine a criminal impersonating your CEO or vendor, requesting an urgent wire transfer that seems completely legitimate. These attacks have cost businesses billions because they exploit trust rather than technology.
Your business partners can unwittingly become your weakness through supply chain attacks. Meanwhile, the threats aren’t all external – insider threats from disgruntled employees or simply careless staff with legitimate access can cause devastating breaches.
And don’t forget those seemingly innocent connected devices. Your smart thermostat, security cameras, or even the office printer can become entry points through IoT vulnerabilities if not properly secured.
Why Hackers Love Small Businesses
There’s a reason cybercriminals have a special fondness for small businesses, and it’s not personal – it’s practical.
Small businesses typically operate with limited resources, often lacking dedicated IT security staff or adequate budget for comprehensive protection. Many run on outdated systems with known vulnerabilities simply because upgrading seems too expensive or disruptive.
Only about half of small business administrators use multi-factor authentication, one of the most effective security measures available. Yet small businesses process valuable customer information, financial data, and intellectual property – all digital gold to attackers.
What’s particularly troubling is that small businesses often serve as gateways to larger targets. By compromising your systems, criminals can potentially access your larger partners or clients.
Most Common Attack Vectors in 2025
The cybersecurity landscape continues to change, but some attack methods have proven particularly effective in 2025.
Social engineering remains cybercriminals’ favorite tool, with phishing accounting for nearly half of all cybercrimes. Why? Because manipulating humans is still easier than breaking sophisticated security systems.
Credential stuffing has become increasingly automated and effective. When credentials from one breach become available, criminals systematically try those username/password combinations across multiple sites, knowing many people reuse passwords.
The rise of artificial intelligence has brought AI-generated attacks that create incredibly convincing phishing attempts custom to specific individuals based on their digital footprint. Meanwhile, as more employees use personal devices for work, mobile device exploitation has become a growing concern.
Finally, the shift to cloud services has created new vulnerabilities through cloud configuration errors. Even minor misconfigurations can leave your data exposed to the world.
Cybersecurity Essentials for Small Businesses: A 10-Step Defense Plan
Let’s face it—thinking about cybersecurity can feel overwhelming when you’re busy running your small business. But protecting your digital assets doesn’t have to be complicated or break the bank. We’ve developed a practical, straightforward approach that any small business owner can implement.
Here’s our real-world, 10-step defense plan that balances protection with practicality:
- Conduct a risk assessment to identify what matters most. Start by understanding what you’re protecting—your customer data, financial records, intellectual property—and where your vulnerabilities lie.
- Deploy network firewalls as your first line of defense. Think of firewalls as the security guards for your digital property, monitoring traffic and keeping the bad actors out.
- Implement endpoint protection on all devices. Every laptop, tablet, or smartphone that connects to your network needs its own shield against malware and other threats.
- Establish patch management routines to keep systems current. Those update notifications you keep ignoring? They often contain critical security fixes that hackers are counting on you to postpone.
- Create a data backup strategy that follows the 3-2-1 rule: three copies of your data, on two different media types, with one copy stored off-site. This is your safety net when other measures fail.
- Encrypt sensitive data both when it’s stored and when it’s being transmitted. Encryption transforms your data into a format that’s useless to anyone without the proper key.
- Enable multi-factor authentication everywhere possible. Passwords alone aren’t enough anymore—adding that second verification step reduces your risk by over 99%, according to Microsoft.
- Implement access controls based on the principle of least privilege. Not everyone in your company needs access to everything—limit permissions to what each person actually needs to do their job.
- Develop an incident response plan because prevention isn’t perfect. When (not if) something happens, having a clear, documented process will significantly reduce damage and recovery time.
- Set up continuous monitoring to catch issues early. Think of this as your security camera system, keeping watch 24/7 for suspicious activity.
For more detailed guidance on putting these steps into action, check out our comprehensive guide on How to Mitigate Cyber Risk.
Step-By-Step Implementation Guide
Taking that first step toward better cybersecurity for small businesses can feel like climbing a mountain. Let’s break it down into manageable steps:
Start with an asset inventory—you can’t protect what you don’t know you have. Document every device, piece of software, and data repository in your business. Don’t forget those “invisible” connected devices like smart thermostats, security cameras, and printers.
Next, perform a vulnerability scan to identify your weak spots. This doesn’t require expensive consultants—CISA (Cybersecurity and Infrastructure Security Agency) offers free scanning services specifically for small businesses.
With this information in hand, develop clear security policies that everyone can understand. Skip the technical jargon and focus on practical guidelines for passwords, acceptable use, and handling sensitive information.
Don’t forget about your business partners. Vendor due diligence is crucial because your security is only as strong as your weakest link. Ask questions about how they protect your data and include security requirements in your contracts.
Finally, prioritize your security investments based on risk, not fear. You don’t need to do everything at once. Address the highest risks first, implement free and low-cost solutions immediately, and plan for more significant investments over time.
Cybersecurity for Small Businesses Toolkit
Government agencies have created several exceptional free resources that can save you thousands in consulting fees:
The FCC Cyberplanner lets you create a custom security plan specific to your business needs. It’s like having a security consultant at your fingertips, without the hourly rate.
CISA Services go beyond just advice—they offer free vulnerability scanning, phishing assessments, and even incident response assistance when things go wrong.
The NIST Small Business Cybersecurity Corner cuts through the technical complexity with guidance specifically written for non-technical business owners.
For busy business owners, the one-page Cybersecurity Tip Sheet from the FCC is gold—it covers the essentials you can implement to dramatically improve your security posture.
People Power: Training, Passwords & MFA
Technology alone can’t protect your business. Your employees are both your greatest vulnerability and your strongest defense against cyber threats.
Building a Human Firewall
Think of your team as your first line of defense—your human firewall. When properly trained, they become your most vigilant security system.
Making training engaging is crucial for retention. Nobody wants to sit through another boring security lecture. That’s why we recommend gamified learning platforms that transform security training into something employees actually look forward to. Simulated phishing exercises with small rewards for those who spot the fakes create healthy competition and real-world skills.
Executive buy-in sets the tone for your entire organization. When leadership visibly participates in security initiatives, employees take notice. Security culture has to flow from the top down.
Regular refreshers keep security top-of-mind. One-and-done training simply doesn’t stick. Quarterly security updates, timely alerts about emerging threats, and brief security moments during team meetings help reinforce good habits.
Creating a reporting culture might be the most valuable outcome of good training. When employees feel comfortable flagging suspicious activity without fear of blame, you gain countless extra sets of eyes watching for threats.
We’ve found that Cybersecurity Awareness Training works best when it connects to employees’ daily work and personal digital lives.
Passwords & Multi-Factor Authentication: Your Front Door Locks
Poor password habits are like leaving your keys in the front door lock—an invitation to trouble. The statistics tell a troubling story: 73% of small business owners struggle to get employees to take password security seriously.
Strong passphrases offer better protection than complex passwords. They’re easier to remember and harder to crack. A passphrase like “correct-horse-battery-staple” is both more memorable and more secure than something like “P@s$w0rd1”.
Password managers eliminate the burden of remembering dozens of complex credentials. These tools generate, store, and auto-fill strong, unique passwords for every site and service your team uses.
Minimum password length matters more than complexity. Requiring at least 12 characters provides significantly better protection against brute force attacks than shorter passwords with special characters.
Multi-Factor Authentication (MFA) is perhaps the single most effective security measure for small businesses. It blocks 99% of automated attacks, even when passwords are compromised. Yet surprisingly, only about half of Azure Active Directory global administrators use MFA themselves.
For the strongest protection, consider FIDO-based authentication like security keys. Unlike text message codes, these physical devices are virtually phishing-proof and remarkably user-friendly.
For more detailed guidance on strengthening your password practices, our article on How Secure Are Your Business Passwords provides practical next steps custom for small business environments.
Planning for the Worst: Compliance, Risk & Incident Response
Even with the best defenses in place, security incidents can still happen. The difference between a minor hiccup and a business-ending disaster often comes down to how well you’ve prepared for that rainy day.
Crafting an Incident Response Playbook
Think of an incident response plan as your business’s emergency procedures—like knowing where the fire extinguishers are before you smell smoke. Here’s how to build one that works:
First, clearly define who’s responsible for what during a crisis. Your team needs designated people handling different aspects of the response:
- Your Incident Commander keeps everyone coordinated and makes the tough calls
- A Technical Lead focuses on containing the threat and getting systems back online
- A Communications Lead handles messaging to employees, customers, and if necessary, the media
- A Legal/Compliance Officer ensures you’re meeting all reporting requirements
Next, map out your incident timeline from detection through recovery. When our clients at Stradiant experience an incident, we walk them through each critical phase: identifying the threat, stopping it from spreading, removing it completely, restoring normal operations, and then learning from what happened.
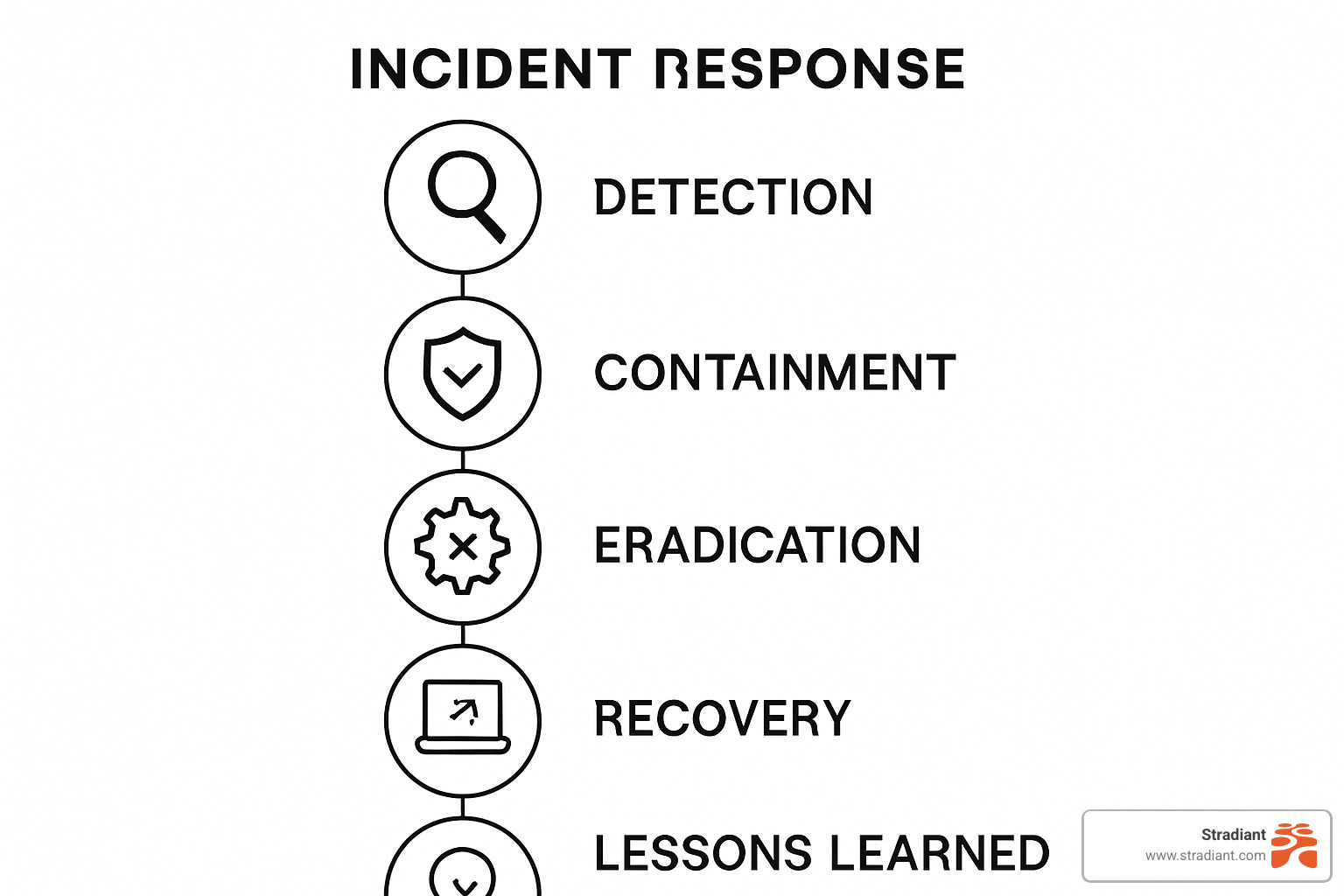
Don’t just create a plan—test it regularly with tabletop exercises. These simulations help identify gaps before a real crisis hits. We’ve seen businesses reduce their recovery time by up to 60% simply by practicing their response quarterly.
Small businesses today also face a growing maze of compliance requirements. Depending on your industry and customer base, you might need to align with standards like NIST SP 800-171 (for federal contractors), CMMC (defense contractors), GDPR (European customers), HIPAA (healthcare), or PCI DSS (credit card processing).
For a deeper dive into understanding your compliance needs, check out our Cybersecurity Risk Assessments page or review the excellent Cyber Guidance for Small Businesses from CISA.
Leveraging Cloud & Managed Services on a Budget
One of the most significant developments for cybersecurity has been the democratization of enterprise-grade security through cloud and managed services.
Cloud-based security offers small businesses several advantages that were once available only to large enterprises. Your data receives automatic updates and patches, benefits from built-in redundancy, and is monitored by professional security teams around the clock.
Managed security services take this approach even further. At Stradiant, we’ve helped countless businesses implement 24/7 monitoring, expert incident response, regular security assessments, and compliance management—all for a predictable monthly fee.
For small businesses in particular, this approach means you can focus on what you do best—running your business—while security experts handle the increasingly complex threat landscape. Learn more about how this integrated approach works in our article on The Value of Unified Cybersecurity and Managed IT.
Frequently Asked Questions about Cybersecurity for Small Businesses
What’s the very first step a small business should take?
If you’re feeling overwhelmed about where to start with cybersecurity for small businesses, begin with a basic risk assessment to understand what you’re protecting and what’s at stake. This doesn’t need to be complicated—even a simple spreadsheet can help tremendously.
Start by listing your critical assets like customer data, financial records, and intellectual property. Note where these assets are stored and who has access to them. Then, consider what would happen if these assets were compromised or lost. How would it impact your operations? Your customers? Your bottom line?
This simple exercise will give you a clear picture of where to focus your initial security efforts. The most vulnerable and valuable assets should get your attention first.
How often should we review and update our security policies?
Security policies should never collect digital dust! Think of them as living documents that need regular care and feeding.
At minimum, conduct a formal review annually. Mark it on your calendar just like you would tax preparation or business planning. But don’t stop there—several events should trigger an immediate policy review:
- After any significant business change (like adopting new software or expanding services)
- When security incidents occur—whether at your business or even a near-miss
- When new regulations affect your industry
- After major breaches in the news that might reveal vulnerabilities you share
Outdated security policies can actually be worse than having none at all because they create a dangerous false sense of security.
What should we do if we suspect a breach?
The moment you suspect your business has been breached, take a deep breath—then act quickly. Your response in the first few hours can dramatically impact the outcome.
First, activate your incident response plan. If you’ve prepared one (and I hope you have!), now’s the time to follow it. Assemble your response team and document everything from the moment of detection.
Next, isolate affected systems to prevent the breach from spreading. Disconnect compromised devices from your network, but don’t power them off immediately—this could destroy valuable forensic evidence.
Be sure to notify key stakeholders promptly. This includes your leadership team and legal counsel. Depending on the situation, you may also need to contact law enforcement and regulatory bodies.
Finally, don’t hesitate to call in the experts. At Stradiant, our incident response team is available 24/7 to help Austin businesses contain breaches and recover quickly. Having professionals determine the extent of the breach and guide your recovery efforts can mean the difference between a minor incident and a business-ending catastrophe.
Your Business, Secure & Resilient: Building a Future Free from Cyber Threats
Cybersecurity isn’t just another item on your to-do list—it’s become essential for your company’s survival and success.
I’ve worked with hundreds of small business owners who initially felt overwhelmed by cybersecurity challenges. Many believed proper protection was beyond their reach financially or technically. The truth is, effective security doesn’t require enterprise-level budgets or an in-house security team.
By implementing the steps we’ve covered in this guide, you can dramatically strengthen your security posture without breaking the bank:
Start by understanding what you’re protecting and where your vulnerabilities lie. This foundation helps you invest resources where they’ll have the greatest impact. Then build your defenses through basic technical controls like firewalls, antivirus solutions, and multi-factor authentication—these alone eliminate the majority of common attacks.
Your team members can be either your greatest vulnerability or your strongest defense. Regular training transforms employees from potential security risks into vigilant guardians of your business data.
No security system is perfect, which is why preparation for incidents is just as important as prevention. A well-crafted incident response plan can mean the difference between a minor disruption and a business-ending disaster.
Think of cybersecurity as an ongoing journey rather than a destination. Start with fundamentals, continuously improve your defenses, and nurture a company culture where everyone understands their role in keeping the business secure.
We’ve guided countless small businesses throughout Austin and Central Texas through this journey. We understand the unique challenges you face—limited budgets, time constraints, and competing priorities. Our approach delivers practical, affordable security strategies custom specifically to small and medium-sized businesses.
Ready to take the next step in protecting your business, customers, and reputation? We’re here to help. Contact us today to learn more about our managed IT services and find how we can help shield your business from evolving cyber threats.

