Cybersecurity risk definition NIST refers to how the National Institute of Standards and Technology defines and standardizes the concept of risk in cybersecurity contexts. According to NIST:
Cybersecurity risk is the effect of uncertainty on or within information and technology, typically considering:
- The potential for loss of confidentiality, integrity, or availability
- The likelihood of threat occurrence
- The magnitude of impact on organizational operations, assets, individuals, other organizations, and the Nation
This definition comes primarily from NISTIR 8286 and is adapted from ISO Guide 73 and NIST SP 800-60 Vol. 1 Rev. 1.
In simpler terms, cybersecurity risk is what might go wrong with your digital systems, how likely it is to happen, and how badly it would hurt your business if it did.
According to the 2023 Verizon Data Breach Investigations Report, 74% of all breaches involved the human element, including social engineering, errors, or misuse. This highlights why understanding and managing cybersecurity risk using standardized frameworks like NIST’s is so critical for organizations of all sizes.
NIST’s approach to risk is particularly valuable because it provides a consistent language and methodology that helps organizations:
- Identify what needs protection
- Assess potential threats and vulnerabilities
- Determine possible impacts
- Develop appropriate safeguards
I’m Joe Dunne, founder and CEO of Stradiant, with extensive experience implementing cybersecurity risk definition NIST frameworks for businesses throughout Austin and surrounding areas, helping organizations understand and effectively manage their cybersecurity risks.

Cybersecurity Risk Definition NIST: The Core Concept
When you strip away all the technical jargon, the cybersecurity risk definition NIST provides is really about understanding what could go wrong in your digital world. NIST defines it as “the effect of uncertainty on or within information and technology” – a simple phrase that carries profound weight for your organization’s security approach.
Think of this definition as resting on three essential pillars:
First, there’s the potential loss of what security pros call the CIA triad – Confidentiality (keeping sensitive data private), Integrity (ensuring information remains accurate and untampered), and Availability (making sure systems work when needed). Any compromise to these elements represents a risk to your business.
Second, there’s likelihood – how probable is it that a threat will actually exploit a vulnerability in your systems? This helps you prioritize where to focus your limited security resources.
Third, there’s impact – what would actually happen if a risk materializes? NIST takes a comprehensive view here, considering effects on your operations, assets, people, other organizations you work with, and sometimes even national interests.
The real-world value of this approach is clear. A 2022 Ponemon Institute study found organizations using risk-based frameworks like NIST reduced their average data breach costs by $1.49 million compared to those without such frameworks. That’s significant savings for simply adopting a more structured approach to security!
Here’s how these components might play out in a typical scenario:
| Component | Example |
|---|---|
| Threat | A sophisticated phishing campaign targeting your employees |
| Vulnerability | Inadequate security awareness training |
| Impact | Unauthorized access to customer data, financial loss, reputational damage |
Using the cybersecurity risk definition NIST provides, you can calculate risk as:
Risk = Likelihood × Impact
This simple formula helps transform abstract security concerns into measurable, manageable priorities.
Breaking Down the Official Wording
When NIST says “effect of uncertainty,” they acknowledge a fundamental truth of cybersecurity: we can never have perfect information. There will always be unknowns, but having a structured approach helps manage this uncertainty rather than being paralyzed by it.
The phrase “on or within information and technology” clarifies that we’re talking specifically about your digital assets and the information they handle.
The “loss of confidentiality, integrity, or availability” refers to the CIA triad I mentioned earlier. Think of confidentiality as keeping your secrets secret, integrity as ensuring your data hasn’t been tampered with, and availability as making sure your systems work when you need them.
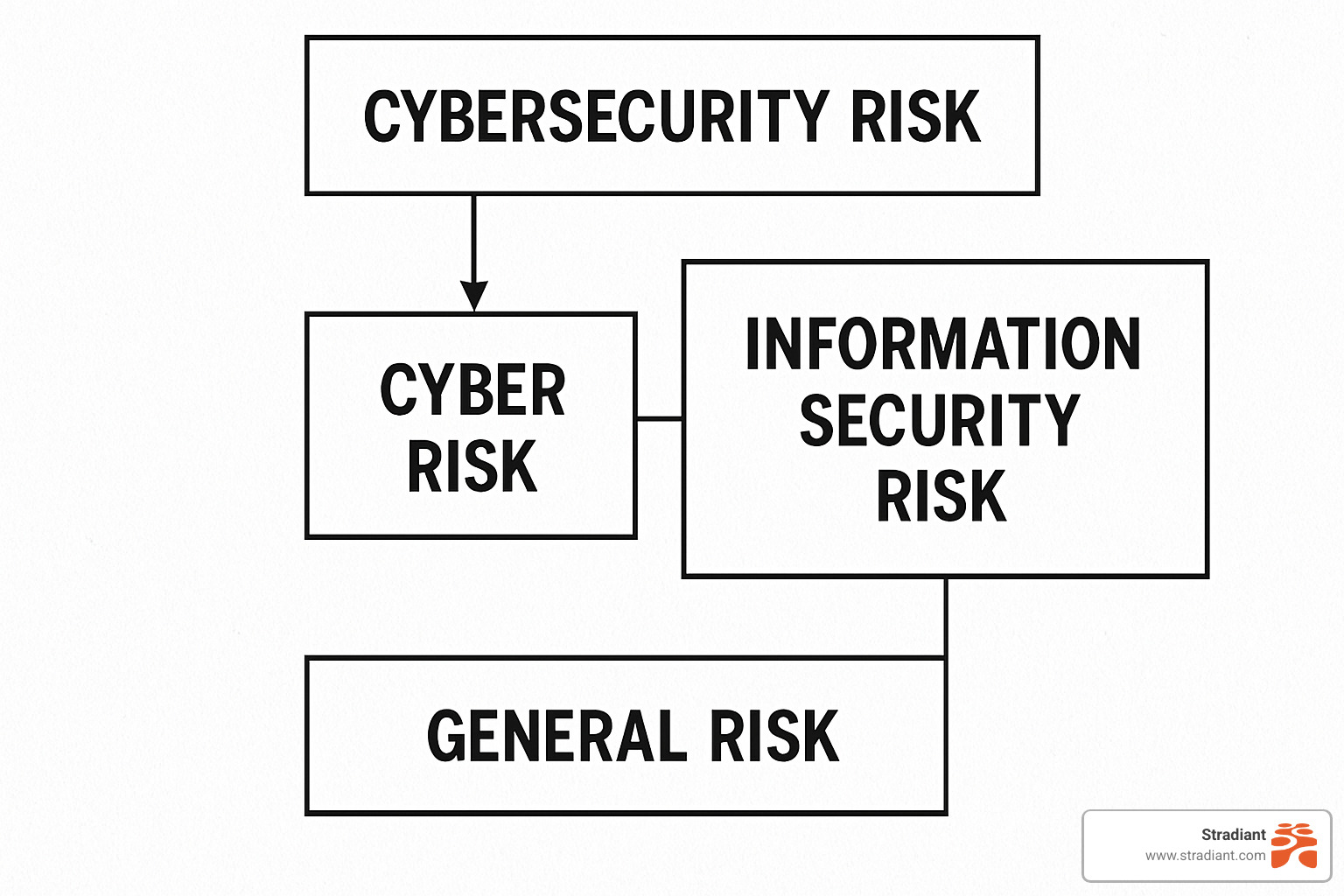
How NIST Distinguishes Its Risk Terms
NIST uses several related but distinct terms that are worth understanding:
Cybersecurity Risk focuses specifically on potential adverse effects coming from digital systems and information.
Risk (General) is broader, defined as “a measure of the extent to which an entity is threatened by a potential circumstance or event.” This applies to all types of organizational risk, not just digital ones.
Cyber Risk is sometimes used interchangeably with cybersecurity risk, but NIST specifically defines it as “the risk of depending on cyber resources” or “the risk of financial loss and operational disruption” due to failures in digital technologies.
Key NIST Publications Shaping the Definition
When you’re trying to understand cybersecurity risk definition NIST, it helps to know which publications to turn to. NIST has created several essential documents that work together like pieces of a puzzle to give us a complete picture of cybersecurity risk management.
SP 800-30: Guide for Conducting Risk Assessments is truly the foundation document in this space. Think of it as your step-by-step playbook for identifying what could go wrong, how likely it is, and what damage it might cause. Many of our clients in Austin find this document particularly helpful because it breaks down complex risk concepts into manageable steps. You can access this essential guide at NIST’s official publication page.
SP 800-37: Risk Management Framework for Information Systems and Organizations takes a broader view by showing how to weave security throughout your entire system development process. Rather than treating security as an afterthought, this approach bakes it in from the beginning—something we’ve found saves businesses significant headaches down the road.
For those looking at the big picture, SP 800-39: Managing Information Security Risk is your go-to resource. It helps you understand risk at three different levels: your entire organization, your business processes, and your individual systems. This tiered approach ensures nothing falls through the cracks.
The NIST Cybersecurity Framework (CSF) has become incredibly popular—and for good reason. A 2022 Gartner survey found that 50% of U.S. organizations use it as the foundation for their security programs. The framework gives you a common language to talk about security risks, which is invaluable when communicating with stakeholders who may not have technical backgrounds.
The newer NISTIR 8286 Series bridges an important gap by connecting cybersecurity risk with broader business risks. This is particularly helpful when you need to explain security concerns to executives who are focused on overall business performance.
Why SP 800-30 Matters for Assessments
I’ve seen how SP 800-30 transforms the way organizations approach risk assessments. This publication doesn’t just tell you what to do—it shows you how to do it through a clear four-step process:
- Prepare for the assessment by defining what you’re looking at and why
- Conduct the assessment by methodically examining threats, vulnerabilities, and impacts
- Communicate results to everyone who needs to know
- Maintain the assessment because security is never “one and done”
What makes SP 800-30 particularly valuable are the practical templates included in its appendices. These ready-to-use forms save you from reinventing the wheel and ensure you don’t miss important aspects of your assessment.
We incorporate these templates and scoring approaches into our Cybersecurity Risk Assessments to give our clients a clear roadmap of their risk landscape.
Risk Appetite & Tolerance in NISTIR 8286 Series
One of the most helpful contributions of the NISTIR 8286 series is how it clarifies the difference between risk appetite and risk tolerance—two terms that are often confused.
Risk appetite is your organization’s overall philosophy toward risk-taking. It’s like deciding whether you’re a conservative investor or someone willing to take chances for potentially bigger rewards. This high-level stance guides all your security decisions.
Risk tolerance, on the other hand, gets into the specifics. It defines exactly how much risk you’ll accept in particular situations.
Applying the NIST Cybersecurity Risk Definition in Practice
Taking the cybersecurity risk definition NIST from theory to reality doesn’t have to be complicated. Let’s break down how you can put these concepts to work in your organization with practical, actionable steps.
Think of cybersecurity risk management as telling a story about what could go wrong. Every good story has key elements, and in this case, they follow a simple pattern:
- Identify threats: The “villains” in your story—phishing attacks, ransomware, or even well-meaning but careless employees
- Spot vulnerabilities: The “weaknesses” that could be exploited—outdated software, weak passwords, or insufficient training
- Understand impacts: The “consequences” if things go wrong—data breaches, operational downtime, or reputational damage
- Assess likelihood: How probable is this particular scenario?
- Calculate risk: Combining likelihood with potential impact
NIST recommends a straightforward formula for documenting these scenarios in NISTIR 8286A:
“[Threat actor] exploits [vulnerability] of [asset], resulting in [adverse impact].”
For example: “An external hacker exploits an unpatched vulnerability in the customer database server, resulting in unauthorized access to customer credit card information.”
This simple structure helps ensure you’re thinking through all the essential elements of each risk scenario.
Once you’ve identified your risks, it’s time to gather them in one place—your risk register. Think of this as your “risk storybook” that includes:
- A unique ID and description for each risk
- The category it falls under
- How likely it is and what impact it would have
- An overall risk rating
- Who’s responsible for managing it
- Your planned response
- Current status and monitoring information
With risks documented, you’ll need to decide what to do about them. Your options include:
- Accepting smaller risks that wouldn’t cause much harm
- Mitigating risks by implementing controls
- Transferring risks through insurance or third-party services
- Avoiding risks by eliminating vulnerable activities entirely
Here in Austin and throughout Central Texas, we help businesses implement these practices through our How to Mitigate Cyber Risk approach. We tailor NIST guidelines to fit your specific business needs and risk tolerance—because no two organizations face exactly the same risks.
Building a NIST-Aligned Risk Register
A well-organized risk register is the heart of effective cybersecurity risk management. Creating one that aligns with the cybersecurity risk definition NIST provides isn’t as daunting as it might seem.
Your risk register should contain these key elements:
Risk Scenarios: Detailed descriptions using the asset-threat-vulnerability-impact structure we discussed earlier. These tell the story of what could happen.
Current Assessment: Your evaluation of how likely this risk is and what impact it would have if it occurred.
Planned Response: What you plan to do about the risk—accept, mitigate, transfer, or avoid.
Status: Where things stand now and what actions are in progress.
Using NIST Templates & Tools
You don’t have to start from scratch—NIST provides plenty of resources to help you implement their guidance:
SP 800-30 Appendices are treasure troves of templates covering everything from threat sources to risk determination. These give you a solid starting point that you can customize to fit your organization.
CSF Profiles help you create “before and after” pictures of your cybersecurity posture. By mapping your current state and desired future state against the framework, you can clearly see what gaps need addressing.
Integrating Cybersecurity Risk into Enterprise Risk Management
When it comes to protecting your business, cybersecurity can’t exist in its own silo. That’s why NISTIR 8286 emphasizes something we at Stradiant have seen firsthand: organizations that connect their cybersecurity risk definition NIST frameworks with broader business risk management simply make better decisions.
Think of it like this – your cybersecurity team might be worried about a software vulnerability, while your finance team is concerned about economic downturns. Both are valid risks, but when viewed together, you get a complete picture that helps you allocate your limited resources more effectively.
By bringing cybersecurity risk into your enterprise risk management (ERM) framework, you’ll experience four major benefits:
First, your security decisions will naturally align with what your business is trying to accomplish. Second, you’ll spend your security dollars where they matter most. Third, technical jargon gets translated into business language everyone understands. And finally, your leadership team can make decisions based on complete information rather than fragments.
This integration isn’t complicated, but it does require intention. Start with a business impact analysis to identify which functions are most critical to your operations. Then, combine your cybersecurity risks with other business risks in a unified register. Create visual dashboards that help executives quickly grasp the situation, and implement continuous monitoring to keep everything current.
Communicating Risk to Leadership
Let’s be honest – one of the biggest challenges in cybersecurity isn’t the technology, it’s getting busy executives to understand why they should care about that critical patch or security upgrade. This is where the cybersecurity risk definition NIST approach really shines.
Heat maps have proven incredibly effective in our work with Austin businesses. These visual tools plot risks by likelihood and impact, giving executives an immediate, intuitive understanding of what needs attention first. When paired with clearly defined tolerance thresholds – the point at which a risk becomes unacceptable – leadership can quickly identify which issues require immediate intervention.
The secret to effective communication isn’t talking about CVE numbers or zero-day exploits. It’s translating technical concerns into business outcomes that executives already care about: “This vulnerability could lead to a $250,000 financial loss” speaks louder than “We have an unpatched RCE vulnerability.”
Continuous Monitoring & Improvement
Cybersecurity isn’t a one-and-done activity – it’s more like gardening than building a fence. NIST SP 800-137 introduces Information Security Continuous Monitoring (ISCM), which is essential for maintaining an accurate understanding of your security landscape as it evolves.
Effective continuous monitoring involves regular vulnerability scans and security checks, tracking how well your controls are working, watching for new threats or changes to your IT environment, and keeping your risk register current with the latest information.
The Federal Trade Commission notes that NIST frameworks are voluntary best practices that can be adapted to businesses of any size, making them accessible even for small businesses without dedicated security teams.
At Stradiant, we’ve built our 24/7 monitoring services specifically to help Austin and Central Texas businesses maintain this continuous improvement cycle. We know that many small and medium businesses don’t have the resources for round-the-clock security teams, which is why we provide that watchful eye, ensuring your risk management stays effective even as threats evolve.
Frequently Asked Questions about NIST
What is the official NIST definition of cybersecurity risk?
When clients ask me about the cybersecurity risk definition NIST provides, I point them to this official wording: “Cybersecurity risk is the effect of uncertainty on or within information and technology, typically considering the potential for loss of confidentiality, integrity, or availability, with impacts on organizational operations, assets, individuals, other organizations, and the Nation.”
This definition comes from NISTIR 8286, drawing on ISO Guide 73 and NIST SP 800-60. What I love about this definition is how it captures the heart of what we’re all worried about – the unknowns in our digital systems and what might go wrong.
NIST SP 800-30 adds another practical angle, explaining that risk typically functions as a combination of how likely a threat might exploit a vulnerability and how badly that would impact your organization. In my years helping Austin businesses secure their systems, this relationship between likelihood and impact has proven to be the most practical way to think about cybersecurity risk.
How do I document cybersecurity risk according to NIST?
Many of our clients initially struggle with documenting their risks in a structured way. NIST recommends using a risk register, which is essentially your central repository for all risk information. Think of it as your risk “source of truth.”
According to NISTIR 8286A, your risk register should include these key elements:
- A unique Risk ID for easy reference
- A detailed Risk Description that follows the asset-threat-vulnerability-impact structure
- The Risk Category (technical, operational, strategic, etc.)
- Your Current Assessment of both likelihood and impact
- Your chosen Risk Response strategy (accept, mitigate, transfer, avoid)
- A specific Response Plan with concrete actions
- The designated Risk Owner responsible for managing the risk
- The current Status of the risk and any response activities
NIST SP 800-30 includes some really helpful templates that can jumpstart your documentation process. We’ve found these templates particularly valuable when helping our clients establish their first formal risk management program.
Your risk register isn’t a “set it and forget it” document. It should be a living record that you update regularly as your threat landscape evolves and your organization changes.
How does risk appetite affect cybersecurity decisions under NIST?
Risk appetite is one of those concepts that sounds abstract but has very concrete implications. It’s essentially your organization’s “risk personality” – how much risk you’re willing to accept to achieve your goals.
According to NISTIR 8286, your risk appetite serves as a guiding principle that influences virtually every cybersecurity decision you make:
Your control selection will be directly shaped by your appetite for risk – organizations with lower risk appetites naturally implement more stringent controls. When we work with healthcare clients, for instance, their low appetite for patient data risks leads to much more comprehensive controls than we might implement for a local retailer.
Your resource allocation decisions flow from your risk appetite – it helps determine how much to invest in cybersecurity relative to other business needs. I’ve seen this play out countless times when helping clients budget for security initiatives.
Your acceptable risk levels are defined by your appetite – it creates the threshold for which risks need mitigation and which can be accepted. This prevents both under-protection and over-protection.
Your response prioritization is guided by risk appetite – it helps you decide which risks to address first when you can’t tackle everything at once (and nobody can!).
Risk appetite statements should come from leadership, with input from security professionals. These high-level statements then cascade down into more specific risk tolerance guidelines that drive day-to-day security decisions.
For example, a statement like “We have zero appetite for risks to customer payment data” might translate to specific requirements for encryption, access controls, and monitoring on all systems touching payment information.
Conclusion
Understanding and applying the cybersecurity risk definition NIST provides isn’t just about checking boxes—it’s about creating a foundation for your organization’s digital safety. The NIST approach gives you a roadmap that makes sense, helping you identify what matters, assess real threats, and manage risks in ways that align with what your business is trying to accomplish.
After diving into NIST’s cybersecurity framework, here’s what really matters:
First, cybersecurity risk is fundamentally about navigating uncertainty. We can’t predict every threat, but we can prepare for the most likely scenarios that could impact our systems and data.
The CIA triad—Confidentiality, Integrity, and Availability—remains the cornerstone of what we’re protecting. When you understand these three elements, you’ve got a clear picture of what’s at stake.
Risk isn’t just about what might happen—it’s about how likely it is combined with how bad it would be if it did happen. This formula helps you prioritize where to focus your limited resources.
Your cybersecurity strategy shouldn’t exist in isolation. When you integrate it with your broader enterprise risk management, you create a unified approach that executives can understand and support.
We work with businesses to implement these NIST-based principles in practical, effective ways. Our team doesn’t just set up systems and walk away—we provide round-the-clock support to ensure your business stays protected as threats evolve.
Effective cybersecurity risk management is a journey, not a destination. By embracing the structured approach that NIST provides, you’ll significantly improve your security posture and reduce the chances of facing costly, disruptive incidents.
Ready to strengthen your approach to cybersecurity risk? We’re here to help. Contact us today for a comprehensive assessment based on NIST guidelines. Our custom solutions provide the protection your business needs without the overwhelming complexity.
For more information about our approach to cybersecurity risk assessments, visit our website or call our Austin office. Let us help you steer the complexities of cybersecurity risk with confidence and peace of mind.