IT security monitoring is the continuous practice of collecting, analyzing, and responding to security events across your organization’s digital infrastructure to detect threats before they cause damage.
Quick Answer – IT Security Monitoring Essentials:
- What it is: Real-time collection and analysis of security logs, network traffic, and system activities
- Core components: SIEM platforms, intrusion detection systems, endpoint monitoring, and automated alerting
- Key benefits: Early threat detection, faster incident response, regulatory compliance, and reduced breach costs
- Implementation: Requires strategic planning, proper tools, trained personnel, and continuous improvement
With cyber threats becoming more sophisticated and costly, the average data breach now costs organizations $4.22 million according to recent industry reports. The question isn’t whether your business will face a cyberattack – it’s whether you’ll detect and stop it in time.
Modern businesses face threats from multiple sources: external hackers deploying advanced malware, insider threats from employees with access to sensitive data, and supply chain vulnerabilities through third-party vendors.
The stakes couldn’t be higher. Companies that experience a major breach underperform by more than 15% on average over three years. For many small and medium businesses, a single successful cyberattack can mean the end of operations entirely.
This is where effective IT security monitoring becomes your digital immune system – constantly learning, adapting, and protecting your business around the clock.
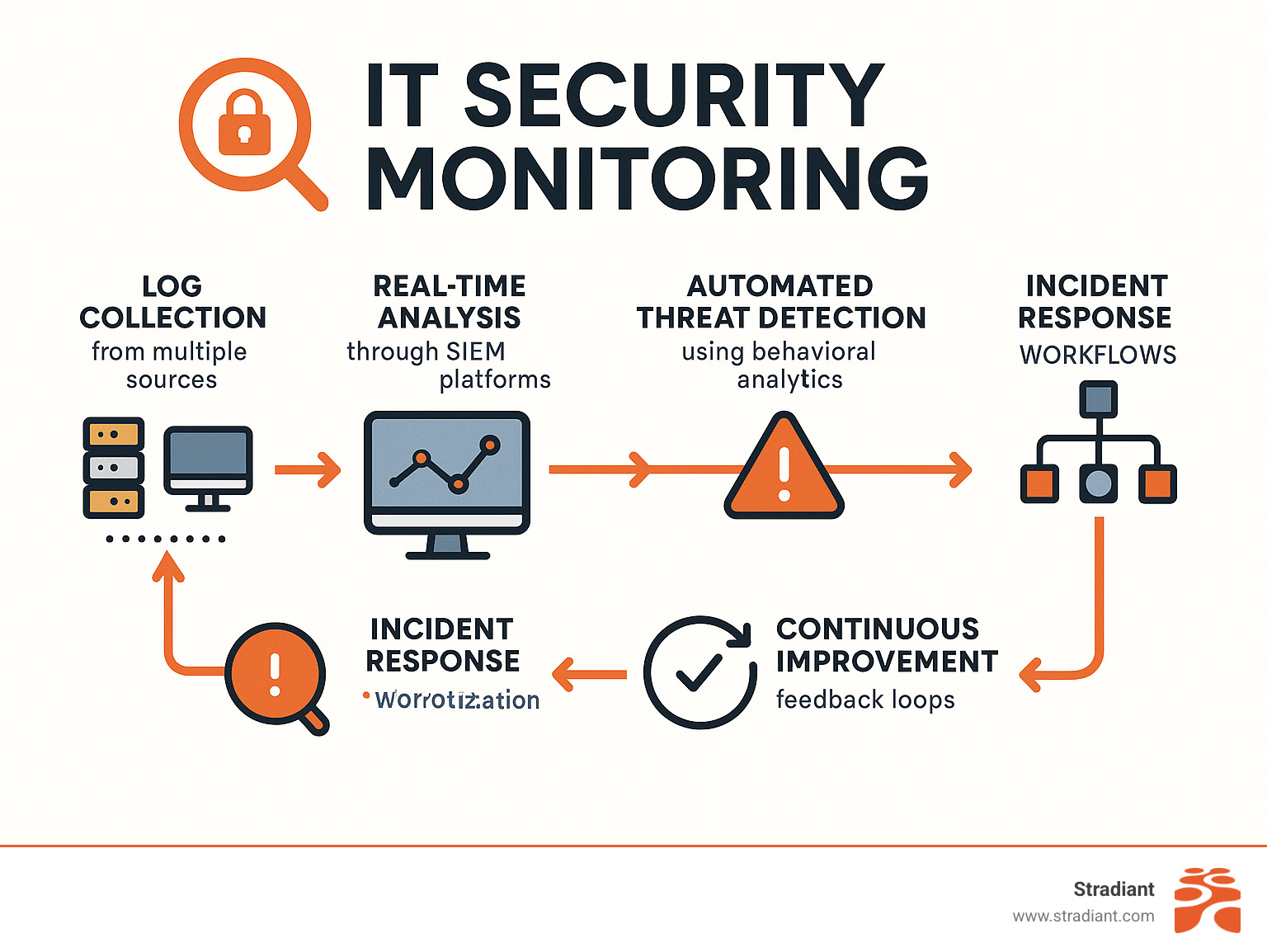
IT Security Monitoring Fundamentals
IT security monitoring is like having a digital security guard who never sleeps, constantly watching your entire digital environment to spot, analyze, and respond to potential security threats as they happen.
The scope of modern security monitoring extends beyond traditional office networks to include cloud environments, remote workers, mobile devices, smart office equipment, and complex vendor relationships.
What is IT security monitoring?
IT security monitoring involves three essential activities:
Log Collection forms the foundation – recording what’s happening across your firewalls, servers, applications, computers, and network devices. Every login attempt, file access, and network connection gets logged.
Anomaly Detection uses behavioral analysis and signature-based detection to spot when something doesn’t look right. Maybe someone’s trying to log in at 3 AM from a foreign country, or a user suddenly starts accessing files they’ve never touched before.
Alerting triggers notifications when potential threats are detected, enabling your team to respond immediately.
Why IT security monitoring matters
Breach costs have skyrocketed to an average of $4.22 million globally. Organizations with proper monitoring detect breaches 76 days faster than those without. That’s the difference between containing a small problem and dealing with a company-ending disaster.
The benefits include rapid response capabilities, business continuity, regulatory compliance, and maintaining customer trust.
SIM vs SEM vs SIEM – key differences
Security Information Monitoring (SIM) focuses on collecting and storing security logs for compliance reporting and historical investigation.
Security Event Monitoring (SEM) emphasizes real-time analysis and immediate threat alerts.
Security Information and Event Management (SIEM) combines both approaches, providing comprehensive log management, real-time threat detection, intelligent correlation, and advanced analytics in one unified platform.
Most businesses today benefit from SIEM solutions because they eliminate complexity while providing more effective threat detection through event correlation.
Building a 360° Monitoring Architecture
Creating comprehensive IT security monitoring requires a layered approach covering every aspect of your digital infrastructure. This architecture should provide complete visibility while remaining manageable and cost-effective.
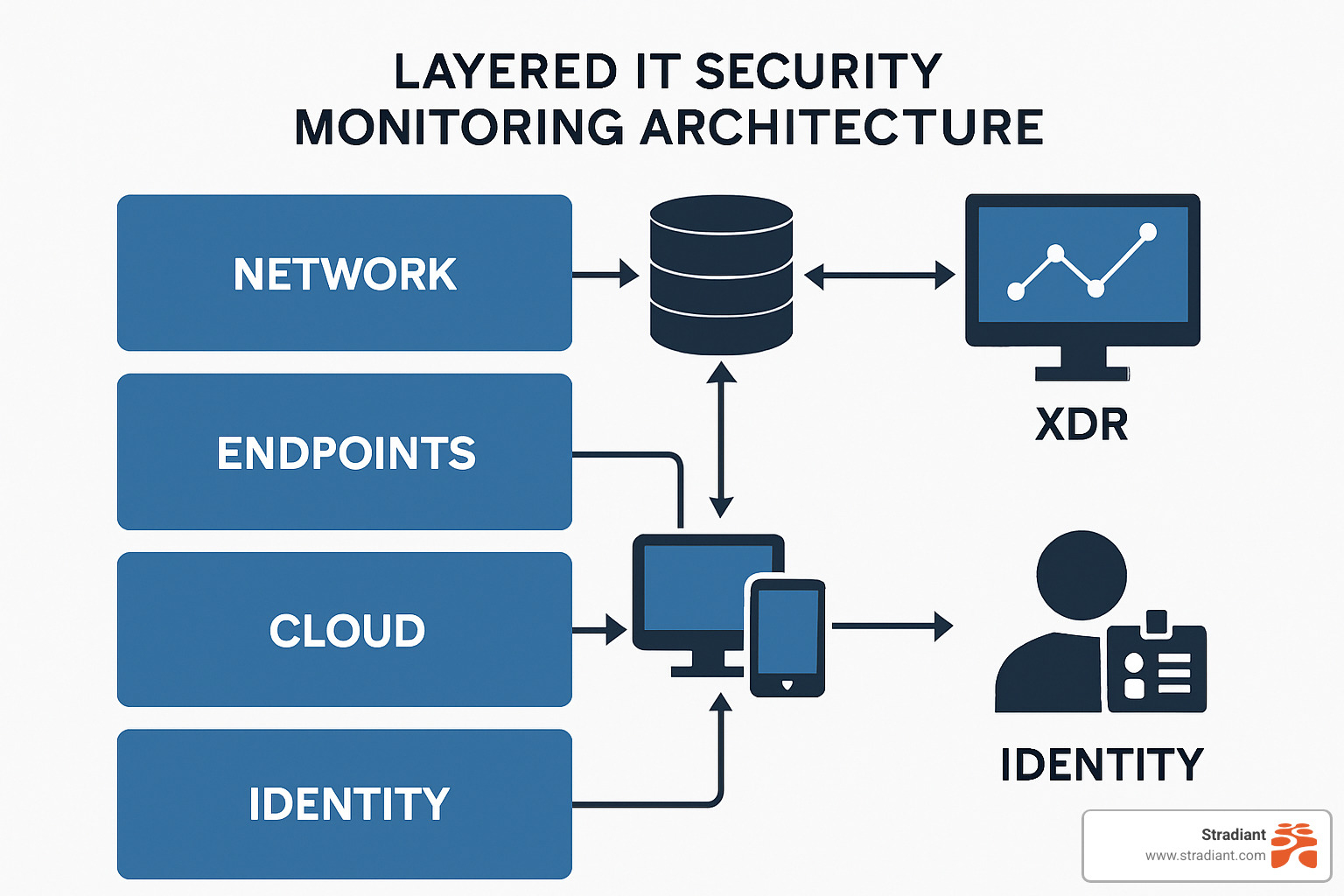
Core components and processes
Effective IT security monitoring relies on four essential processes:
Collection gathers data from network sensors monitoring internet traffic, endpoint agents watching individual devices, cloud APIs tracking online services, and identity telemetry following user access patterns.
Normalization converts different-formatted data into standardized formats for proper analysis.
Correlation connects related events to identify complex attack patterns that might look innocent individually but reveal malicious intent when viewed together.
Prioritization ranks alerts based on severity and business impact, preventing alert fatigue while ensuring critical threats get immediate attention.
Selecting the right tools & technologies
SIEM platforms serve as the foundation, providing centralized log management, correlation, and alerting capabilities.
Intrusion Detection and Prevention Systems (IDS/IPS) monitor network traffic for malicious activity and can automatically block threats.
Endpoint Detection and Response (EDR) solutions focus on monitoring individual devices for malware, suspicious processes, and unauthorized access.
Security Orchestration, Automation, and Response (SOAR) platforms automate incident response workflows and integrate multiple security tools.
For businesses looking to build comprehensive monitoring, we recommend starting with a Cybersecurity Risk Assessment to identify your specific monitoring needs and priorities.
Unified platforms & integration benefits
Modern unified platforms offer significant advantages over managing separate tools:
Single pane of glass reduces complexity by consolidating multiple tools into one interface, dramatically improving efficiency.
Reduced Mean Time to Response (MTTR) follows from better integration, enabling faster investigation and response times.
Better correlation capabilities emerge when all security data flows through integrated systems, leading to more accurate threat detection and fewer false positives.

Automating Detection and Response with Continuous Monitoring
Modern automated monitoring systems provide security that never sleeps, never takes breaks, and gets smarter every day. Since cyber threats don’t follow business hours, continuous automated monitoring has become essential.
Advantages of automated, continuous monitoring
Real-time alerts represent the biggest game-changer. When a threat is detected, automated systems flag it within seconds rather than hours or days.
Machine learning dramatically reduces false positives by learning what normal looks like in your environment – understanding that certain employees always log in early, backup systems run on specific schedules, and applications naturally generate more traffic during busy periods.
Proactive defense capabilities allow systems to automatically isolate suspicious devices, block malicious IP addresses, or quarantine infected files while alerting your team for follow-up investigation.
Incident response & remediation workflow
Effective IT security monitoring guides you through solving problems systematically:
Containment happens first – preventing threats from spreading by disconnecting affected systems, disabling compromised accounts, or blocking suspicious traffic.
Eradication completely removes threats from all affected systems, requiring thoroughness since attackers often plant multiple backdoors.
Recovery focuses on safely restoring normal operations with extra monitoring to ensure threats haven’t returned.
Post-incident review provides valuable lessons about your defenses, processes, and team readiness.
Consider implementing Cybersecurity Awareness Training to ensure everyone understands their responsibilities during security incidents.
Case studies & real-world lessons
The Equifax disaster went undetected for 76 days because an expired SSL certificate prevented their monitoring system from working. This oversight contributed to exposing 147 million records and cost over $700 million.
Supply chain attacks like SolarWinds changed how we think about monitoring – attackers walked in through trusted vendor software updates, requiring monitoring of unusual behavior from trusted applications.
Insider threats present the trickiest challenge, requiring detection of subtle behavioral changes from people who already have legitimate system access.
The key insight is that monitoring requires both sophisticated tools and human expertise working together seamlessly.
Governance, Compliance & KPIs
Proper governance and metrics prove whether your IT security monitoring is actually working and meeting legal obligations.
Meeting compliance requirements
PCI-DSS requires continuous monitoring of cardholder data environments plus regular vulnerability scanning.
HIPAA mandates audit controls and monitoring of electronic protected health information with 72-hour breach notification requirements.
NIST Framework provides excellent continuous monitoring guidelines that work across industries.
GDPR requires breach detection and reporting within 72 hours for businesses handling European customer data.
The CISA Security Monitoring service offers additional guidance for understanding effective monitoring practices.
Measuring success of IT security monitoring
Mean Time to Detect (MTTD) measures how quickly you spot threats. Industry average is around 200 days – good monitoring should reduce this to hours or minutes.
Mean Time to Respond (MTTR) tracks response speed once threats are detected. Every minute counts when containing breaches.
Alert Fidelity measures what percentage of alerts are real threats versus false alarms. Good systems achieve 85% or higher fidelity rates.
Coverage Ratios show what percentage of infrastructure is actually monitored – this should approach 100% for critical systems.

Best practices checklist
Implement least privilege monitoring by watching for privilege escalation and unauthorized access attempts.
Maintain patch cadence by tracking patch deployment across all systems.
Keep asset inventory current by monitoring all devices, applications, and services.
Continuous improvement means regularly reviewing and updating monitoring rules and procedures.
Regular testing through tabletop exercises validates whether monitoring actually works when it matters.
Overcoming Implementation Challenges
Implementing IT security monitoring can feel overwhelming, but challenges become manageable with the right approach.
Common problems & mitigation tips
Data overload is the biggest challenge. Focus on high-value events like failed login attempts, privilege escalations, and unusual network traffic patterns rather than collecting everything.
Alert fatigue occurs when systems cry wolf constantly. Modern systems use behavioral analytics to learn your environment’s normal patterns, dramatically reducing false positives.
Skills shortage in cybersecurity is real. Start by training existing IT staff on security fundamentals, then supplement with external expertise. Cross-training creates more resilient security than relying on single specialists.
Legacy systems can’t always support modern monitoring agents, but network-based monitoring can watch traffic patterns and behavior even without direct software installation.
Leveraging managed services & MSSPs
Managed Security Service Providers offer practical ways to get enterprise-grade IT security monitoring without enterprise budgets.
Round-the-clock expertise means threats get detected and addressed even when your office is closed.
Cost sharing makes advanced tools affordable by spreading costs across multiple clients.
Scalability becomes effortless – expanding monitoring doesn’t require hiring staff or buying new licenses.
Future trends to watch
AI-driven analytics are becoming sophisticated at learning subtle attack patterns beyond known signatures.
Zero-trust architecture assumes nothing is safe until proven otherwise, requiring continuous monitoring of every user, device, and application.
Extended Detection and Response (XDR) platforms break down silos between security tools, providing unified threat views.
Behavioral analytics improve at detecting insider threats by identifying behavioral deviations from normal patterns.

The key is starting with solid fundamentals, then adapting as new capabilities become available.
Frequently Asked Questions about IT Security Monitoring
How quickly should alerts be investigated?
Critical alerts demand immediate attention – 15 to 30 minutes maximum for active malware infections, unauthorized admin access, or data exfiltration attempts.
High-priority alerts should be investigated within 1 to 4 hours, including failed login attempts from unusual locations or suspicious network traffic.
The secret is having clear severity levels established before alerts start appearing. Medium and low-priority alerts can wait 8 to 24 hours but shouldn’t pile up indefinitely.
What data should be logged and for how long?
Capture authentication attempts, network connections, file access events, system configuration changes, and application activities.
Retention periods vary by industry. Healthcare organizations might need six years or more for HIPAA compliance. For most small to medium businesses, 90 days to one year covers basics and satisfies most compliance frameworks.
Cloud-based solutions make long-term storage much more manageable than maintaining massive on-premise systems.
Can small businesses afford enterprise-grade monitoring?
Cloud-based monitoring solutions have changed the game completely. Instead of buying expensive hardware and hiring full-time analysts, you can access Fortune 500-level technology through managed services.
Managed security service providers spread costs across multiple clients, making sophisticated monitoring accessible to modest IT budgets.
The real question isn’t whether you can afford proper monitoring – it’s whether you can afford not to have it. Modern managed services eliminate major barriers that used to keep small businesses from enterprise-grade protection.
Your Path to Stronger IT Security Monitoring
IT security monitoring isn’t something you can postpone. Every business faces the same reality: cyber threats don’t take weekends off, and they don’t care about budget constraints.
Start with what matters most. Begin by understanding your current vulnerabilities and monitoring gaps. Focus on fundamentals first: collecting security logs from critical systems, setting up basic automated alerts, and having a clear incident response plan.
Think of it like building a house – establish a solid foundation before adding sophisticated features. Get the basics rock-solid, then gradually add more advanced capabilities as your program grows.
Remember: this isn’t a “one and done” project. Effective monitoring requires ongoing attention, regular updates, and continuous learning. New threats emerge constantly, and your monitoring must evolve alongside them.
Every day without proper monitoring is another day of unnecessary risk – risk that could cost you everything you’ve worked to build.
At Stradiant, we understand that IT security monitoring isn’t just about technology – it’s about protecting your livelihood, your employees’ jobs, and your customers’ trust. Our approach focuses on solutions that actually fit your business, not cookie-cutter packages.
Our 24/7 support means you’re never facing a security incident alone. When alerts fire at 2 AM on a Sunday, experienced professionals handle the situation while you sleep.
Ready to stop worrying about what might happen and start focusing on growing your business? Learn more about our managed IT services and find how we help businesses across Central Texas sleep better at night.
The best time to implement proper security monitoring was yesterday. The second-best time is right now.

