Small business IT solutions encompass the technology services, tools, and support systems that keep your operations running smoothly while protecting against cyber threats. Here’s what every small business needs:
Essential IT Solutions:
• Managed IT Services – Proactive monitoring and maintenance
• Cybersecurity Protection – Multi-layered defense against threats
• Data Backup & Recovery – Automated, secure data protection
• Cloud Services – Scalable storage and collaboration tools
• Help Desk Support – Quick resolution of technical issues
• Network Management – Reliable connectivity and performance
The stakes have never been higher for small businesses relying on technology. According to recent industry data, 80% of small businesses have suffered IT-related downtime, with costs ranging from $82,200 to $256,000 for a single event. Meanwhile, nearly 50% of small businesses face cyberattacks annually, with recovery costs averaging close to $1 million.
Yet 68% of small business owners don’t have a written disaster recovery plan, leaving them vulnerable to devastating losses. The reality is stark: one malware attack can cripple an unprepared small business.
Modern small businesses need more than just computers and internet access. You need proactive protection, reliable support, and scalable solutions that grow with your business. The right IT strategy isn’t just about fixing problems—it’s about preventing them while enabling growth and maintaining customer trust.
I’m Joe Dunne, founder and CEO of Stradiant, where I help organizations understand and manage their cybersecurity risks in Austin and the surrounding area. Having served as IT Director at major restaurant chains before launching my consultancy, I’ve seen how the right small business IT solutions can transform operations and protect against costly disruptions.
Why Reliable Tech Is Mission-Critical
Let’s talk about something that keeps many business owners up at night: what happens when your technology fails? The answer isn’t pretty, and the numbers might surprise you.
The Real Cost of Downtime
Here’s a sobering fact: downtime costs small businesses up to $427 per minute. That’s not a typo. For a typical 25-employee business, even a four-hour outage can cost over $100,000 in lost revenue, employee wages, and recovery efforts.
These aren’t just scary statistics—they represent real businesses struggling to recover from preventable IT failures. When your systems crash, you’re not just dealing with frustrated employees staring at blank screens. You’re watching potential customers walk away, deals fall through, and your hard-earned reputation take a hit.
Think about the ripple effects for a moment. Your customers can’t place orders. Your team can’t access critical files. Your phones might stop working. In today’s always-connected world, even a brief outage sends customers straight to competitors who keep their systems running smoothly.
Productivity and Customer Trust
Beyond the immediate financial punch, outdated technology creates a constant productivity drain. Research shows that two-thirds of workers report outdated technology significantly impacts their productivity. Even worse, over 40% say it affects their job satisfaction, which translates to higher turnover rates—another expensive problem.
Customer trust is incredibly fragile. When your systems fail during critical moments—processing payments, handling service requests, or protecting sensitive data—you risk permanent damage to those relationships. This is exactly why small businesses in Austin need custom IT support that prevents these disasters before they happen.
Compliance and Regulatory Requirements
Many small businesses must meet strict regulatory requirements for data protection. Whether it’s HIPAA for healthcare, PCI DSS for payment processing, or industry-specific mandates, non-compliance can result in devastating fines or even business closure.
Proper small business IT solutions ensure you meet these requirements without the headaches. Nobody wants to explain to customers why their personal information was compromised because of outdated security measures.
Return on Investment
Here’s the good news: investing in reliable IT delivers measurable returns. Companies using comprehensive managed services report significant improvements in system reliability, security posture, and employee productivity. One retail operation achieved 5x ROI over three years by replacing their patchwork of IT tools with professional managed services.
The math is simple: preventing one major outage often pays for an entire year of proactive IT support. When you factor in improved productivity, reduced stress, and better customer satisfaction, reliable technology becomes one of your best business investments.
Core Small Business IT Solutions at a Glance
Think of small business IT solutions like the foundation of your house—you need all the pieces working together, not just random patches here and there. The most successful businesses I work with understand that technology isn’t about collecting the latest gadgets. It’s about creating a seamless system that actually helps you run your business better.
Building on Solid Ground: Proactive Support
Here’s the thing about waiting for technology to break before fixing it—it’s like never changing your car’s oil and then acting surprised when the engine seizes up. Traditional “break-fix” IT support puts you in constant fire-fighting mode, always one step behind the next crisis.
Proactive support flips this script entirely. Instead of waiting for disasters, we’re monitoring your systems around the clock, catching problems before they become problems. Your computers get their updates automatically, security patches happen seamlessly, and performance issues get resolved before you even notice them.
It’s the difference between running a smooth operation and constantly explaining to customers why your systems are down. Trust me, your stress levels will thank you for making this switch.
The Cloud Revolution That Actually Matters
Remember when every business needed a server room that sounded like a jet engine and cost a fortune to maintain? Those days are thankfully behind us. Cloud infrastructure lets small businesses access the same enterprise-grade technology that big corporations use, without the massive upfront costs or ongoing headaches.
With cloud services, your team can access files and applications from anywhere—whether they’re working from the office, home, or that coffee shop down the street. Updates happen automatically, backups are built-in, and you’re not stuck maintaining expensive hardware that becomes outdated faster than you can say “tax write-off.”
Cybersecurity That Actually Works
Cybersecurity isn’t just about installing antivirus software and hoping for the best anymore. Modern threats require multiple layers of protection working together like a well-coordinated defense team. This means endpoint protection on every device, network monitoring that watches for suspicious activity, email filtering to catch phishing attempts, and user training so your team knows what to watch for.
The goal isn’t to build an impenetrable fortress—it’s to make your business a harder target than the competition. Cybercriminals are (usually) lazy; they’ll move on to easier targets when faced with proper defenses.
Data Protection That Lets You Sleep at Night
Here’s a sobering thought: if your business data disappeared tomorrow, how long would it take to get back up and running? For many businesses, the answer is “we’d be out of business.” That’s exactly why automated backup systems aren’t optional anymore—they’re as essential as business insurance.
Modern data backup and recovery solutions work quietly in the background, creating multiple copies of your important files and storing them both locally and in the cloud. When disaster strikes—whether it’s a ransomware attack, hardware failure, or natural disaster—you can restore everything quickly and get back to serving customers.
Managed vs. Break-Fix: Which Small Business IT Solutions Win?
Let me share something I’ve learned after years in this business: the way you approach IT support fundamentally shapes your entire business experience. The choice between managed services and break-fix support isn’t just about cost—it’s about whether you want to run your business or constantly worry about it.
Why Break-Fix Feels Like a Trap
Break-fix support seems appealing at first glance. You only pay when something breaks, right? What could be more fair than that? Well, here’s what actually happens in the real world.
Emergency IT repairs typically cost between $125-$250 per hour, and they always seem to happen at the worst possible times. Your email server crashes on Friday afternoon, or your payment system goes down during your busiest sales period. You’re stuck waiting for a technician who doesn’t know your systems, paying premium rates, while your business bleeds money.
The real kicker? Break-fix providers have no incentive to prevent problems. In fact, they make more money when your systems fail more often. It’s like hiring a mechanic who gets paid more when your car breaks down—the incentives are completely backwards.
The Managed Services Difference
Managed IT services vs break-fix IT services isn’t even a fair comparison once you understand the fundamental difference in approach. With managed services, you’re paying for prevention, not just repairs.
For typically $100-$200 per user monthly, you get comprehensive coverage that includes proactive monitoring, regular maintenance, security updates, and 24/7 support. More importantly, you get predictable costs that you can budget for, instead of surprise emergency bills that can wreck your cash flow.
The managed approach means issues get identified and resolved before they impact your business. That failing hard drive? We replace it during off-hours before it crashes. That security vulnerability? It gets patched automatically before hackers can exploit it.
Prevention Beats Reaction Every Time
Think about it this way: would you rather have a smoke detector that warns you about fires, or a fire department that only shows up after your building is already burning? Managed services are like having a whole team of smoke detectors, fire suppressors, and safety experts working around the clock to prevent disasters.
This proactive approach doesn’t just save money—it saves your sanity. You can focus on growing your business instead of constantly worrying about the next technology crisis.
Co-Managed Models to Extend Small Business IT Solutions
Growing businesses often find themselves in an interesting spot. You’ve hired someone with technical skills to handle day-to-day IT needs, but you’re starting to realize that one person can’t possibly cover everything. That’s where co-managed IT services come in—and they’re perfect for businesses that want the best of both worlds.
Filling the Gaps Your Internal Team Can’t Cover
Your internal IT person might be great at helping employees with software issues and managing daily operations, but what happens when you need specialized cybersecurity expertise? Or when a critical system fails at 2 AM on Sunday? Or when you’re planning a major technology upgrade and need strategic guidance?
Co-managed services complement your existing team rather than replacing them. We handle the complex stuff—24/7 monitoring, advanced security management, strategic planning, and specialized projects—while your internal person focuses on user support and day-to-day operations.
Recent surveys show that 37.9% of small and medium businesses use this co-managed approach, and it’s easy to see why. You get enterprise-level expertise without the enterprise-level salary costs.
Virtual CIO Services for Strategic Thinking
Here’s something most small businesses don’t realize they need until it’s too late: strategic technology leadership. A virtual Chief Information Officer (vCIO) provides the big-picture thinking that prevents costly mistakes and aligns your technology investments with your business goals.
Instead of just solving today’s problems, a vCIO helps you plan for tomorrow’s opportunities. They conduct quarterly business reviews, create technology roadmaps, help with budget forecasting, and manage vendor relationships. It’s like having a senior executive focused on technology strategy, without the six-figure salary.
Making Shared Responsibilities Work
The key to successful co-managed relationships is clearly defining who does what. Typically, your internal team handles the front-line user support and daily operations they’re already familiar with, while we manage the behind-the-scenes infrastructure monitoring, security oversight, and strategic planning.
This division plays to everyone’s strengths. Your team maintains those important direct relationships with users, while we provide the specialized expertise and round-the-clock coverage that keeps everything running smoothly. It’s a partnership that scales with your business and evolves as your needs change.
The Essential Services Checklist for Small Businesses
Building a solid technology foundation for your small business isn’t about buying the latest gadgets—it’s about having the right services working together to protect and empower your team. Think of it like building a house: you need a strong foundation before you can add the fancy features.
Let’s walk through the essential services every small business needs to stay secure, productive, and competitive.
Cybersecurity Protection: Your Digital Fortress
Cyber security isn’t optional anymore—it’s as essential as locking your doors at night. The challenge is that standard antivirus software alone detects no more than 25% of modern threats. You need multiple layers working together like a digital fortress.
Your cybersecurity foundation should include endpoint protection with next-generation antivirus on every device, network security through firewalls and intrusion detection, and email filtering to catch phishing attempts before they reach your inbox. Don’t forget the human element—regular user training helps your team spot threats that technology might miss.
Multi-factor authentication adds crucial extra security to all business accounts, while dark web monitoring alerts you when your business data appears where it shouldn’t. These layers work together to create comprehensive protection that adapts to evolving threats.
Data Backup and Recovery: Your Business Insurance Policy
Data backups & data recovery services protect your business’s most valuable asset—its data. Think of backups as insurance you hope never to use but desperately need when disaster strikes.
Modern backup solutions provide automated daily backups without relying on anyone remembering to press a button. Your data should live in multiple locations—both local and cloud storage—so you’re protected even if one location fails. But here’s the crucial part: regular testing ensures your backups actually work when you need them most.
Rapid recovery capabilities mean you can restore individual files or entire systems quickly, while disaster recovery planning provides documented procedures for various emergency scenarios. Backup costs typically range from $50-$150 per server monthly for basic protection, scaling to $200-$300 monthly for comprehensive cloud-based solutions.
Cloud Migration Support: Moving Without the Chaos
Moving to cloud services can transform your business operations, but only if it’s done right. Professional migration support ensures minimal downtime through careful scheduling and execution, while maintaining complete data integrity throughout the transfer.
Proper security configuration sets up access controls and encryption correctly from day one. Your team receives user training on new cloud-based workflows, and ongoing optimization continuously improves performance and manages costs.
Help Desk and User Support: Your Technology Lifeline
When technology problems arise—and they will—responsive support keeps your team productive instead of frustrated. Quality help desk services offer multiple contact methods including phone, email, chat, and remote assistance, with initial response within 15 minutes for urgent issues.
Skilled, certified technicians who understand your specific business environment provide better support than generic call centers. Issue tracking documents and follows up on all support requests, while ongoing user training helps your team make the most of available tools.
Basic help desk support typically costs $50-$100 per user monthly, while comprehensive support ranges from $100-$200 per user monthly—a small price for keeping your team productive.
Network Monitoring and Management: Preventing Problems Before They Start
24/7 network monitoring provides continuous oversight of performance and security, with automated alerts for immediate notification of potential problems. This proactive approach includes performance optimization through regular tuning and capacity planning to ensure resources meet growing demands.
Security monitoring detects unauthorized access attempts or suspicious activity before they become serious breaches. Network management services typically cost $100-$500 monthly for basic monitoring, scaling to $500-$1,000 monthly for advanced 24/7 monitoring with rapid response.
Mobile Device Management: Securing Work Everywhere
With remote work becoming standard, managing smartphones and tablets is crucial for security. Device encryption protects data on mobile devices, while remote wipe capability secures information when devices are lost or stolen.
Application management controls which apps can access business data, configuration enforcement ensures all devices meet security standards, and usage monitoring provides insights into how devices access business resources.
Regulatory Compliance Support: Meeting Industry Requirements
Many businesses must meet specific regulatory requirements that aren’t optional. HIPAA compliance protects healthcare data, PCI DSS compliance secures payment card processing, and SOX compliance handles financial reporting requirements.
Whether you need industry-specific regulations or custom compliance for your business sector, proper small business IT solutions ensure you meet these requirements while maintaining operational efficiency. Get help from a partner to steer complex compliance requirements.
The key is having all these services work together seamlessly, creating a technology environment that supports your business goals rather than creating obstacles. When properly implemented, these essential services provide the foundation for sustainable growth and peace of mind.
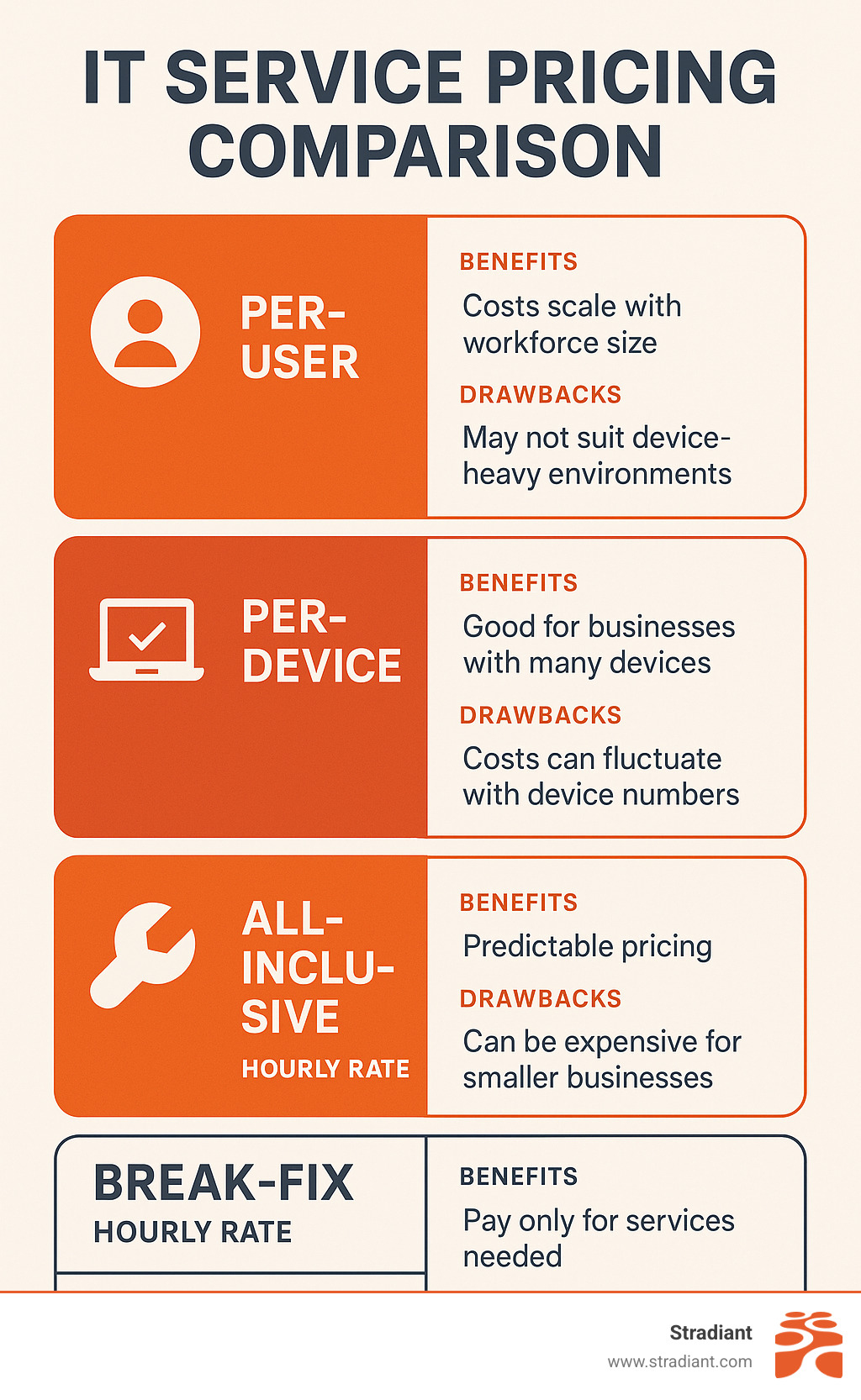
Budgeting & Choosing the Right Provider
Let’s be honest—figuring out IT costs can feel like decoding a foreign language. One provider quotes per user, another charges by device, and a third throws out a flat rate that sounds too good to be true. Don’t worry; I’ll help you make sense of it all.
Understanding Common Pricing Models
Most small business IT solutions providers use one of four main pricing approaches. Per-user pricing is the most popular, typically running $75-$150 monthly per employee for basic services or $100-$200 for comprehensive coverage. This model grows naturally with your team and makes budgeting straightforward.
Per-device pricing charges based on how many computers, servers, and mobile devices need management. This works well if you have lots of equipment but fewer employees, typically costing $50-$100 per device monthly.
Some providers offer all-inclusive fixed fees ranging from $1,200-$3,500 monthly regardless of your team size. This gives you maximum cost predictability but might not scale efficiently as you grow.
Then there’s the old-school break-fix hourly model at $125-$250 per hour. While it seems economical upfront, break-fix cost data shows this often becomes the most expensive option when emergencies strike at the worst possible moments.
| Pricing Model | Monthly Cost | Best For | Pros | Cons |
|---|---|---|---|---|
| Per-User | $100-$200/user | Growing teams | Scalable, predictable | Can get expensive with large teams |
| Per-Device | $50-$100/device | Equipment-heavy businesses | Matches actual hardware | Complex with mixed device types |
| All-Inclusive | $1,200-$3,500 | Stable organizations | Maximum predictability | May overpay if underutilizing |
| Break-Fix | $125-$250/hour | Very small businesses | Low upfront cost | Unpredictable, expensive emergencies |
Watch Out for Hidden Costs
Good providers are upfront about pricing, but some costs naturally fall outside monthly service fees. Software licensing for tools like Microsoft 365 or specialized business applications typically costs extra. Hardware purchases aren’t usually included in service agreements, though many providers help with procurement.
Project work like major system migrations or new office setups often involves separate charges. Some providers also charge travel fees for on-site visits, especially if you’re outside their primary service area.
The key is finding providers who clearly explain what’s included versus what costs extra. Nobody likes billing surprises.
Service Level Agreements Matter
Your Service Level Agreement (SLA) defines what you can expect from your provider. Look for clear response time commitments—quality providers typically respond to urgent issues within 15-30 minutes, even if resolution takes longer.
Uptime guarantees should promise at least 99.5% network availability. Security incident response procedures should be clearly documented, including escalation processes for serious threats.
These aren’t just legal documents—they’re your protection against providers who overpromise and underdeliver.
Calculating Your Return on Investment
Here’s where the math gets interesting. If your business generates $500,000 annually, each hour of downtime costs roughly $250 in lost revenue. Preventing just one four-hour outage yearly justifies significant IT investment.
Employee productivity improvements often provide the biggest returns. When outdated technology slows down a $50,000 annual salary employee by 10%, you’re losing $5,000 yearly per person. Modern small business IT solutions typically boost productivity by 15-25%.
Security incident costs average nearly $1 million for small businesses. Comprehensive protection costing $50,000 annually provides excellent ROI if it prevents major incidents.
Choosing Your Technology Partner
The right provider becomes a true business partner, not just a vendor. Look for industry experience relevant to your business—providers familiar with your sector understand specific compliance requirements and common challenges.
Local presence matters for on-site support, but don’t discount national providers with strong remote capabilities. Many businesses benefit from hybrid approaches combining local relationships with 24/7 remote monitoring.
Security credentials like CompTIA Security+, CISSP, or vendor-specific certifications demonstrate commitment to current security practices. Customer references from similar businesses provide honest insights about response times, communication quality, and overall satisfaction.
Most importantly, choose a provider who scales with your growth. What works for 10 employees should efficiently expand to 50 or 100 employees without requiring complete service overhauls.
The investment in quality small business IT solutions pays dividends through improved productivity, reduced downtime, and protection against costly security incidents. Take time to find the right partner—your business’s future depends on it.
Cloud, Security & Remote Work Best Practices
Modern businesses require integrated approaches to cloud adoption, cybersecurity, and remote work support. These technologies work together to create flexible, secure, and productive work environments.
Zero-Trust Security Architecture
Traditional security models assumed everything inside your network was safe. Zero-trust architecture assumes nothing is safe and verifies every access request, regardless of location or device.
Key zero-trust principles include:
- Verify every user and device: Multi-factor authentication for all access
- Least privilege access: Users only access resources they specifically need
- Continuous monitoring: Ongoing verification of user and device behavior
- Micro-segmentation: Isolating network resources to limit breach impact
This approach is particularly important for remote work, where employees access business resources from various locations and devices.
Multi-Factor Authentication (MFA)
MFA provides additional security beyond passwords by requiring multiple verification methods. Common factors include:
- Something you know: Passwords or PINs
- Something you have: Smartphones, hardware tokens, or smart cards
- Something you are: Fingerprints, facial recognition, or other biometrics
Implementing MFA reduces successful cyberattacks by over 99%, making it one of the most effective security investments available.
Encrypted Backup Strategies
Modern backup solutions must protect data both in transit and at rest through encryption:
- End-to-end encryption: Data encrypts before leaving your premises
- Zero-knowledge architecture: Even backup providers can’t access your data
- Immutable backups: Protected copies that can’t be modified or deleted by ransomware
- Geographic distribution: Copies stored in multiple physical locations
These features ensure your backups remain accessible even during sophisticated cyberattacks targeting backup systems.
Hybrid Work Infrastructure
Supporting both office and remote workers requires careful infrastructure planning:
- Reliable internet connectivity: Redundant connections prevent single points of failure
- VPN or zero-trust network access: Secure remote connections to business resources
- Cloud-based collaboration tools: Platforms that work equally well from any location
- Unified communications: Phone, video, and messaging systems accessible anywhere
SD-WAN for Multi-Location Businesses
Software-Defined Wide Area Networks (SD-WAN) simplify connectivity between multiple business locations:
- Centralized management: Configure all locations from a single dashboard
- Automatic failover: Traffic routes around failed connections automatically
- Quality of service: Prioritize critical applications over less important traffic
- Cost optimization: Use multiple internet providers for redundancy and cost savings
SD-WAN solutions are particularly valuable for businesses with multiple offices or significant remote workforces.
Small Business IT Solutions for Secure Cloud Adoption
Cloud migration offers tremendous benefits but requires careful planning to maintain security and optimize costs.
Migration Planning
Successful cloud migrations follow structured approaches:
- Assessment: Catalog current applications, data, and dependencies
- Strategy selection: Choose between lift-and-shift, re-platforming, or complete rebuilding
- Security design: Plan access controls, encryption, and monitoring
- Migration execution: Move systems in phases to minimize disruption
- Optimization: Continuously improve performance and costs
Professional migration services ensure minimal downtime and proper security configuration throughout the process.
SaaS Governance
Software-as-a-Service applications proliferate quickly in growing businesses. Proper governance includes:
- Application inventory: Tracking all SaaS subscriptions and users
- Access management: Controlling who can access which applications
- Data protection: Ensuring sensitive information remains secure
- Cost optimization: Eliminating unused subscriptions and optimizing licensing
- Compliance monitoring: Verifying applications meet regulatory requirements
Without proper governance, SaaS sprawl can create security vulnerabilities and unnecessary costs.
Cost Optimization Strategies
Cloud services offer flexibility but require active management to control costs:
- Right-sizing resources: Matching computing power to actual needs
- Reserved capacity: Committing to longer terms for significant discounts
- Automated scaling: Adjusting resources based on demand patterns
- Regular audits: Identifying and eliminating unused resources
- Multi-cloud strategies: Using different providers for different workloads
The benefits of working with managed IT services include ongoing cloud cost optimization as part of comprehensive service packages.
Small Business IT Solutions That Power Remote & Hybrid Teams
Remote and hybrid work models require robust technical infrastructure to maintain productivity and security.
VPN and Network Access
Secure remote access protects business resources while enabling flexible work arrangements:
- Site-to-site VPN: Connecting remote offices to main locations
- Client VPN: Individual device connections for remote workers
- Zero-trust network access: Modern alternative to traditional VPNs
- Split tunneling: Routing only business traffic through secure connections
Modern solutions provide seamless user experiences while maintaining strong security controls.
Collaboration Suite Integration
Comprehensive collaboration platforms integrate multiple communication and productivity tools:
- Email and calendaring: Shared scheduling and communication
- File sharing and co-authoring: Real-time document collaboration
- Video conferencing: High-quality meetings with screen sharing
- Team messaging: Instant communication with file sharing
- Project management: Task tracking and workflow automation
Popular platforms like Microsoft 365 and Google Workspace provide integrated solutions that work consistently across devices and locations.
Endpoint Security for Remote Devices
Remote devices face increased security risks requiring comprehensive protection:
- Endpoint detection and response (EDR): Advanced threat monitoring and response
- Device encryption: Full-disk encryption for laptops and mobile devices
- Remote wipe capabilities: Protecting data on lost or stolen devices
- Patch management: Automated security updates for all devices
- Application control: Restricting unauthorized software installations
These protections ensure remote devices maintain the same security standards as office-based equipment.
Wi-Fi and Connectivity Assessments
Reliable internet connectivity is crucial for remote work success. Professional assessments evaluate:
- Bandwidth requirements: Ensuring sufficient capacity for video calls and file transfers
- Network reliability: Identifying potential connectivity issues
- Security configuration: Proper router and Wi-Fi security settings
- Performance optimization: Maximizing available bandwidth efficiency
Frequently Asked Questions About Small Business IT
What’s the average monthly cost of outsourced IT for a 25-user company?
If you’re running a 25-person business, you’re probably wondering what proper IT support will actually cost you. The honest answer? Comprehensive managed IT services typically run between $2,500-$5,000 monthly for a company your size. That breaks down to roughly $100-$200 per user each month.
Now, before you feel sticker shock, let me explain what you’re actually getting for that investment. This isn’t just someone to call when your computer crashes. Your monthly fee covers 24/7 monitoring and support, meaning we’re watching your systems around the clock and fixing problems before they impact your business. You’re also getting multi-layered cybersecurity protection that includes endpoint security, email filtering, and training for your team to spot threats.
Data backup and recovery services ensure your business information is always protected and recoverable. Plus, you get unlimited help desk support for your users and strategic planning sessions where we review your technology roadmap quarterly to ensure it aligns with your business goals.
That software licensing costs—like Microsoft 365 or specialized security tools—typically aren’t included in these base prices. Hardware purchases and major project work (like office moves or system overhauls) usually involve separate charges too.
Here’s the thing though: this investment almost always pays for itself. The productivity gains, prevented downtime, and avoided security incidents more than justify the monthly cost. Compare that to break-fix support at $125-$250 per hour during emergencies, and managed services start looking like a bargain pretty quickly.
How do I know if managed or co-managed support fits my growth plans?
This is one of the most common questions I hear from business owners, and the answer really depends on where you are now and where you’re headed.
Go with fully managed IT services if you don’t have dedicated IT staff on your team, your current team lacks cybersecurity expertise, or you simply want to focus on running your business instead of managing technology. Managed services also make sense if you need round-the-clock support coverage and prefer predictable monthly costs over surprise emergency bills.
Co-managed services work better when you already have some IT staff who need backup and specialized expertise. Maybe you have a tech-savvy office manager who handles basic computer issues, but you need expert help with cybersecurity, cloud migrations, or strategic planning. This model lets you keep internal control while accessing high-level expertise for complex projects.
I often recommend co-managed services for growing businesses with 20-100 employees. You maintain those important internal relationships while getting specialized knowledge for areas beyond your team’s expertise. It’s particularly valuable if you’re growing rapidly and need flexible support that can adapt quickly.
Think about your three-year growth plans too. If you expect to double in size, make sure whichever provider you choose can scale their services without forcing you to completely change your IT support model. The last thing you want is to outgrow your IT partner just when you need them most.
What first steps should I take to strengthen cybersecurity today?
I get this question a lot, and I love it because it shows business owners are taking security seriously. The good news is that you can make dramatic improvements to your security posture with some simple steps you can implement today.
Start with multi-factor authentication on all your business accounts. This means email, banking, cloud services—everything important. It takes just a few minutes to set up, but it prevents over 99% of automated attacks. That’s probably the biggest security bang for your buck you’ll ever get.
Train your team about cybersecurity threats. Most successful attacks happen because someone clicked a malicious link or downloaded a suspicious attachment. Spend an hour educating your employees about phishing emails and social engineering tactics. Human error causes most security breaches, so this training is incredibly cost-effective.
Get your passwords sorted out. Require strong, unique passwords for all business accounts, and seriously consider implementing a password manager. It makes using secure passwords much easier for everyone while dramatically improving your security.
Turn on automatic updates for all your devices and software. I know, I know—updates can be annoying. But most successful cyberattacks exploit known vulnerabilities that already have available patches. Staying current with updates closes these security holes automatically.
Implement automated daily backups of your essential business data. More importantly, test those backups to make sure they actually work when you need them. This protects you against both ransomware attacks and simple hardware failures.
Finally, review who has access to what in your business systems. Remove access immediately for former employees and contractors—you’d be surprised how often this gets overlooked. For current team members, make sure they only have access to the resources they actually need for their jobs.
These steps provide immediate security improvements while you work on developing a more comprehensive cybersecurity strategy. If you want a deeper dive into your specific vulnerabilities, a professional security assessment can identify risks unique to your business environment and help prioritize your next security investments.
Conclusion
The right small business IT solutions aren’t just about fixing computers when they break—they’re about building a foundation that lets your business thrive. Think of it like having a reliable car versus one that leaves you stranded on the highway. You want technology that gets you where you’re going, not headaches that slow you down.
After helping countless Austin businesses steer their technology challenges, I’ve seen the same pattern repeatedly. Companies that invest in proper IT infrastructure early avoid the costly disasters that blindside their unprepared competitors. It’s not about having the fanciest gadgets—it’s about having systems that work when you need them most.
The Reality Check
Here’s what we’ve learned: proactive beats reactive every single time. Waiting for problems to surface costs far more than preventing them in the first place. When your server crashes at 2 AM or ransomware locks up your files, emergency repairs become expensive lessons in why prevention matters.
Security isn’t optional anymore—it’s survival. With cyberattacks costing small businesses nearly $1 million on average, comprehensive protection pays for itself by preventing just one major incident. Your customers trust you with their information, and that trust evaporates quickly when data breaches make headlines.
Integration makes the difference between technology that helps and technology that hurts. Random software solutions held together with digital duct tape create more problems than they solve. The best results come from coordinated systems that work together seamlessly.
Your Path Forward
Start with an honest assessment of where you stand today. Do your current systems support your growth plans, or are they holding you back? Can you sleep soundly knowing your data is protected and your team can work productively from anywhere?
The essential services checklist we’ve covered gives you a roadmap. You don’t need to implement everything overnight, but you do need a plan that addresses your biggest vulnerabilities first. Strategic planning prevents the expensive mistakes that derail growing businesses.
Consider scheduling a comprehensive IT assessment to identify gaps in your current setup. This evaluation reveals vulnerabilities you might not even know exist and opportunities to improve efficiency. Most business owners are surprised by what they find during these reviews.
Building for Tomorrow
Technology keeps evolving, but the fundamentals stay constant: reliable systems, strong security, and expert support. Get these right, and you’re positioned to adapt to whatever changes come next. Skip them, and you’ll spend your time fighting fires instead of growing your business.
Here in Austin, we understand the unique pressures facing local businesses. You’re competing with companies that have enterprise-level resources, but you need solutions that fit small business budgets. That’s where the right IT partner makes all the difference.
At Stradiant, we’ve built our reputation on providing enterprise-grade protection with the personal attention small businesses deserve. Our 24/7 expert support means you’re never alone when technology challenges arise. We combine cutting-edge cybersecurity technology with the kind of responsive service that builds lasting partnerships.
Whether you need comprehensive managed services, specialized cybersecurity protection, or strategic technology planning, we’re here to help you steer the complex world of business technology. Get a custom quote for managed IT services and find how the right IT partner can transform your daily operations.
Don’t wait for a crisis to force your hand. Technology failures and security breaches always happen at the worst possible moments. Take control of your IT infrastructure now, while you can make thoughtful decisions instead of desperate ones.
Your business deserves technology that works as hard as you do. Let’s make that happen.